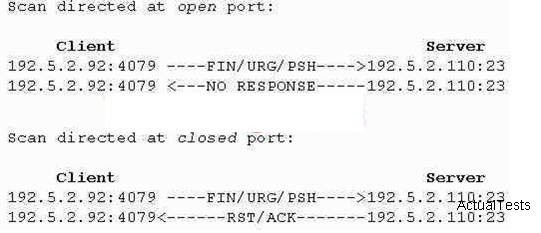
What type of scan is Hayden attempting here?
Hayden iis the network security administrator for her company, a large marking firm based in Miami. Hayden just got back from a security conference in Las Vegas where they talked about all kinds of old and new security threats; many of which she did not know of. Hayden is worried about the current security threats; many of which she did not know of. Hayden is worried about the current security state of her company’s network so she decides to start scanning the network from an external IP address. To see how some of the hosts on her network react, she sends out SYN packets to an IP range. A number of IPs responds with a SYN/ACK response.Before the connection is established she sends RST packets to those hosts to stop the session. She has done this to see how her intrusion detection system will log the traffic. What type of scan is Hayden attempting here?
Which Type of scan sends a packets with no flags set?
Which Type of scan sends a packets with no flags set? Select the Answer
Which type of scan does not open a full TCP connection?
Which type of scan does not open a full TCP connection?
How can you modify your scan to prevent triggering this event in the IDS?
While performing ping scans into a target network you get a frantic call from the organization’s security team. They report that they are under a denial of service attack. When you stop your scan, the smurf attack event stops showing up on the organization’s IDS monitors. How can you modify your scan to prevent triggering this event in the IDS?
Which of the following scan options can help you achieve this?
You are scanning the target network for the first time. You are able to detect few conventional open ports. While attempting to perform conventional service identification by connecting to the open ports, the scan yields either bad or no results. As you are unsure of the protocols in use, you want to discover as many different protocols as possible. Which of the following scan options can help you achieve this?
What type of scan is Jessica going to perform?
Jessica works as systems administrator for a large electronics firm. She wants to scan her network quickly to detect live hosts by using ICMP ECHO Requests. What type of scan is Jessica going to perform?
If Lori is supposed to scan all known TCP ports, how many ports should she select in the software?
Lori has just been tasked by her supervisor toonduct vulnerability scan on the corporate network.She has been instructed to perform a very thorough test of the network to ensure that there are no security holes on any of the machines.Lori’s company does not own any commercial scanning products, so she decides to download a free one off the Internet.Lori has never done a vulnerability scan before, so she is unsure of some of the settings available in the software she downloaded.One of the options is to choose which ports that can be scanned.Lori wants to do exactly what her boss has told her, but she does not know what ports should be scanned.
If Lori is supposed to scan all known TCP ports, how many ports should she select in the software?