Which of the following is the most secure encryption protocol that the network administrator should recommend?
A person approaches a network administrator and wants advice on how to send encrypted email
from home. The end user does not want to have to pay for any license fees or manage server
services. Which of the following is the most secure encryption protocol that the network
administrator should recommend?
A _______________device is used for uniquely recognizing humans based upon one or more intrinsic physical or b
CORRECT TEXT
Fill in the blank with the appropriate term. A _______________device is used for uniquely
recognizing humans based upon one or more intrinsic physical or behavioral traits.
…is the complete network configuration and information toolkit that uses multi-threaded and multi-connec
CORRECT TEXT
Fill in the blank with the appropriate term. ——————————- is the complete network
configuration and information toolkit that uses multi-threaded and multi-connection technologies in
order to be very fast and efficient.
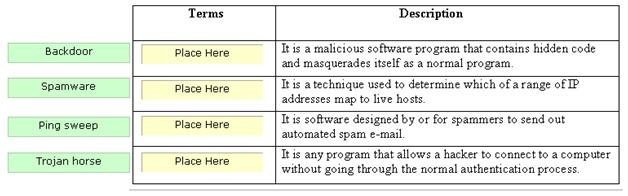
Drag and drop the terms to match with their descriptions.
His program is vulnerable to a __________ attack
John works as a C programmer. He develops the following C program:
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
int buffer(char *str) {
char buffer1[10];
strcpy(buffer1, str);
return 1;
}
int main(int argc, char *argv[]) {
buffer (argv[1]);
printf(“Executed\n”);
return 1;
}
His program is vulnerable to a __________ attack.
Which of the following analyzes network traffic to trace specific transactions and can intercept and log traff
Which of the following analyzes network traffic to trace specific transactions and can intercept and
log traffic passing over a digital network? Each correct answer represents a complete solution.
Choose all that apply.
which of the following conditions does the system enter ROM monitor mode?
In which of the following conditions does the system enter ROM monitor mode? Each correct
answer represents a complete solution. Choose all that apply.
Which of the following protocols is used for exchanging routing information between two gateways in a network
Which of the following protocols is used for exchanging routing information between two gateways
in a network of autonomous systems?
Which of the following is a 16-bit field that identifies the source port number of the application program in
Which of the following is a 16-bit field that identifies the source port number of the application
program in the host that is sending the segment?
______________________ is typically carried out by a remote attacker attempting to gain information or access
CORRECT TEXT
Fill in the blank with the appropriate term. ______________________ is typically carried out by a
remote attacker attempting to gain information or access to a network on which it is not authorized
or allowed.