The two halves are hashed individually. If the password is 7 characters or less, than the second half of the h
LAN Manager passwords are concatenated to 14 bytes, and split in half. The two halves are hashed individually. If the password is 7 characters or less, than the second half of the hash is always:
If Lori is supposed to scan all known TCP ports, how many ports should she select in the software?
Lori has just been tasked by her supervisor toonduct vulnerability scan on the corporate network.She has been instructed to perform a very thorough test of the network to ensure that there are no security holes on any of the machines.Lori’s company does not own any commercial scanning products, so she decides to download a free one off the Internet.Lori has never done a vulnerability scan before, so she is unsure of some of the settings available in the software she downloaded.One of the options is to choose which ports that can be scanned.Lori wants to do exactly what her boss has told her, but she does not know what ports should be scanned.
If Lori is supposed to scan all known TCP ports, how many ports should she select in the software?
Hackers usually control Bots through…?
Hackers usually control Bots through:
What Internet registry should Bill look in to find the IP address?
Bill has started to notice some slowness on his network when trying to update his company’s website and while trying to access the website from the Internet. Bill asks the help desk manager if he has received any calls about slowness from the end users, but the help desk manager says that he has not. Bill receives a number of calls from customers that cannot access the company website and cannot purchase anything online. Bill logs on to a couple of his routers and notices that the logs show network traffic is at an all time high. He also notices that almost all the traffic is originating from a specific address.
Bill decides to use Geotrace to find out where the suspect IP is originates from. The Geotrace utility runs a traceroute and finds that the IP is coming from Panama. Bill knows that none of his customers are in Panama so he immediately thinks that his company is under a Denial of Service attack. Now Bill needs to find out more about the originating IP address.
What Internet registry should Bill look in to find the IP address?
What is the first character that Bob should use to attempt breaking valid SQL request?
Bob has been hired to do a web application security test. Bob notices that the site is dynamic and must make use of a back end database. Bob wants to see if SQL Injection would be possible. What is the first character that Bob should use to attempt breaking valid SQL request?
What can Angela's IT department do to get access to the education website?
Angela is trying to access an education website that requires a username and password to login. When Angela clicks on the link to access the login page, she gets an error message stating that the page cannot be reached. She contacts the website’s support team and they report that no one else is having any issues with the site. After handing the issue over to her company’s IT department, it is found that the education website requires any computer accessing the site must be able to respond to a ping from the education’s server. Since Angela’s computer is behind a corporate firewall, her computer cannot ping the education website back.
What can Angela’s IT department do to get access to the education website?
Which TCP and UDP ports must you filter to check null sessions on your network?
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
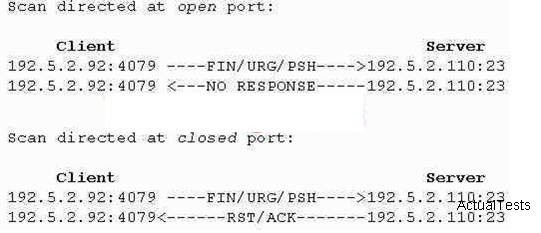
What type of port scan is shown below?
How can he generate traffic on the network so that he can capture enough packets to crack the WEP key?
Derek has stumbled upon a wireless network and wants to assess its security. However, he does not find enough traffic for a good capture. He intends to use AirSnort on the captured traffic to crack the WEP key and does not know the IP address range or the AP. How can he generate traffic on the network so that he can capture enough packets to crack the WEP key?
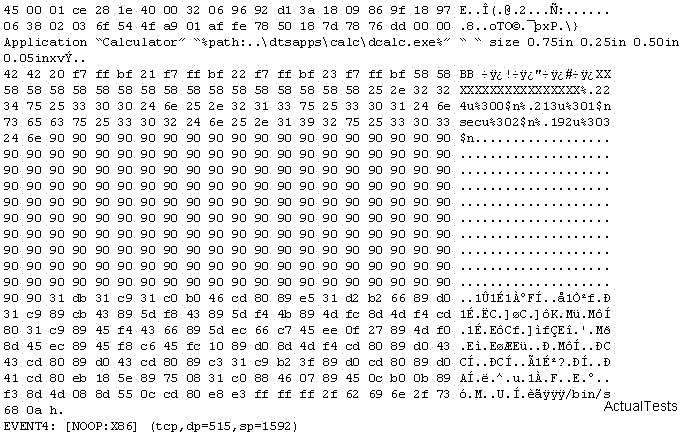
an analyst what would you conclude about the attack?
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack. You also notice “/bin/sh” in the ASCII part of the output. As an analyst what would you conclude about the attack?