Which of the following types of interoperability agreem…
A company has decided to move large data sets to a cloud provider in order to limit the costs of new
infrastructure. Some of the data is sensitive and the Chief Information Officer wants to make sure both parties
have a clear understanding of the controls needed to protect the data.
Which of the following types of interoperability agreement is this?
Which of the following describes the purpose of an MOU?
Which of the following describes the purpose of an MOU?
Which of the following is the GREATEST security risk of…
Which of the following is the GREATEST security risk of two or more companies working together under aMemorandum of Understanding?
Which of the following poses the greatest risk with thi…
Users can authenticate to a company’s web applications using their credentials from a popular social media
site. Which of the following poses the greatest risk with this integration?
Which of the following would be a possible solution to …
The system administrator notices that their application is no longer able to keep up with the large amounts of
traffic their server is receiving daily. Several packets are dropped and sometimes the server is taken offline.
Which of the following would be a possible solution to look into to ensure their application remains secure and
available?
which of the following data security concerns?
Elastic cloud computing environments often reuse the same physical hardware for multiple customers over time
as virtual machines are instantiated and deleted. This has important implications for which of the following data
security concerns?
Which of the following concepts are included on the thr…
Which of the following concepts are included on the three sides of the “security triangle”? (Choose three.)
Which of the following should Sara do to address the risk?
Sara, the Chief Security Officer (CSO), has had four security breaches during the past two years.
Each breach has cost the company $3,000. A third party vendor has offered to repair the security hole in the
system for $25,000. The breached system is scheduled to be replaced in five years.
Which of the following should Sara do to address the risk?
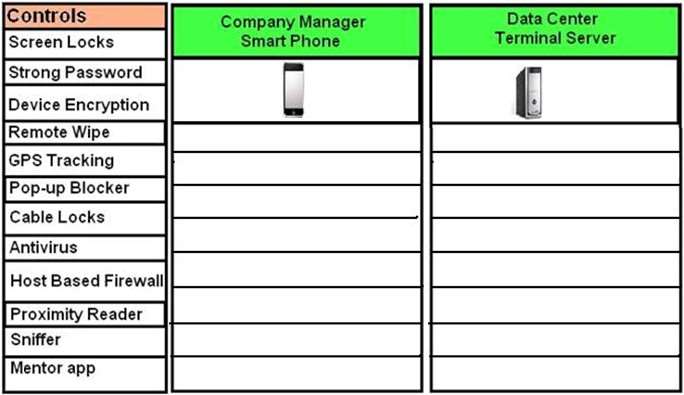
Drag and Drop the applicable controls to each asset type.
DRAG DROP
A Security administrator wants to implement strong security on the company smart phones and terminal
servers located in the data center. Drag and Drop the applicable controls to each asset type.
Instructions: Controls can be used multiple times and not all the placeholders need to be filled. When you have
completed the simulation, Please Choose Done to submit.
Select and Place:
Which of the following defines a business goal for syst…
Which of the following defines a business goal for system restoration and acceptable data loss?