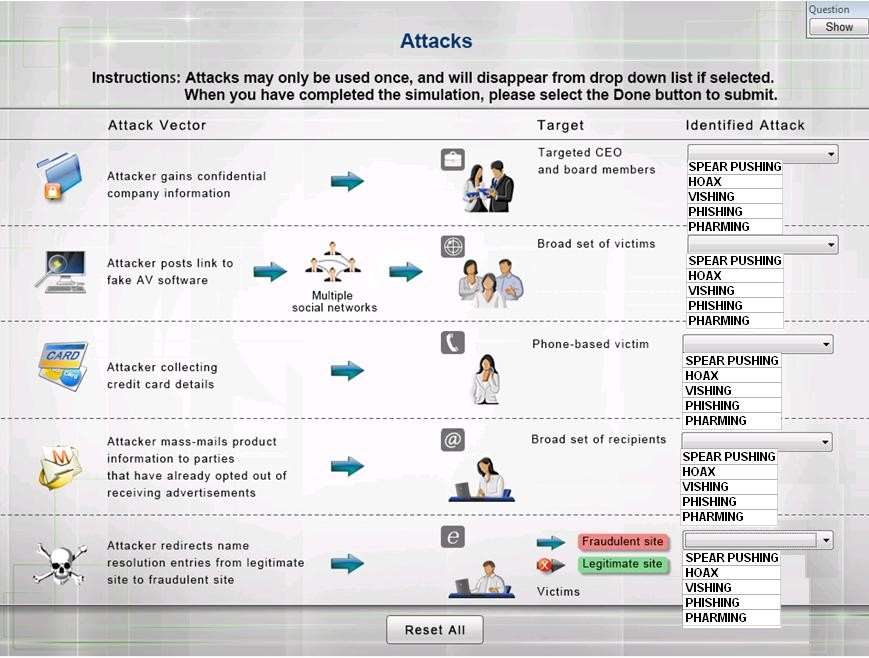
Select the appropriate attack from each drop down list to label…
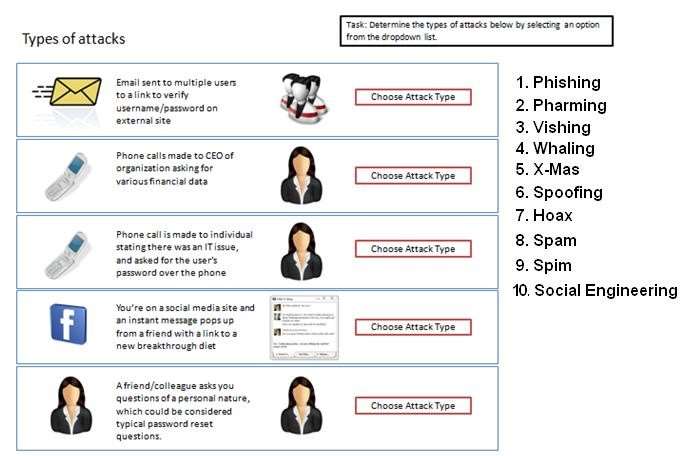
Determine the types of attacks below by selecting an option from…
Which of the following attacks is occurring?
A server with the IP address of 10.10.2.4 has been having intermittent connection issues. The logs show
repeated connection attempts from the following IPs:
10.10.3.16
10.10.3.23
212.178.24.26
217.24.94.83
These attempts are overloading the server to the point that it cannot respond to traffic. Which of the following
attacks is occurring?
which is difficult to reverse engineer in a virtual lab?
Which of the following describes a type of malware which is difficult to reverse engineer in a virtual lab?
Which of the following types of malware is on Ann’s wor…
A user, Ann, is reporting to the company IT support group that her workstation screen is blank other than a
window with a message requesting payment or else her hard drive will be formatted. Which of the following
types of malware is on Ann’s workstation?
Which of the following explains the difference between …
Pete, a security analyst, has been tasked with explaining the different types of malware to his colleagues. The
two malware types that the group seems to be most interested in are botnets and viruses.
Which of the following explains the difference between these two types of malware?
Which of the following malware types is MOST likely to …
Which of the following malware types is MOST likely to execute its payload after Jane, an employee, has left
the company?
Which of the following is this an example of?
Ann, a software developer, has installed some code to reactivate her account one week after her account has
been disabled. Which of the following is this an example of? (Choose two.)
Which of the following should the CIO be concerned with?
The Chief Information Officer (CIO) receives an anonymous threatening message that says “beware of the 1st
of the year”. The CIO suspects the message may be from a former disgruntled employee planning an attack.
Which of the following should the CIO be concerned with?
Which of the following is this an example of?
Two programmers write a new secure application for the human resources department to store personal
identifiable information. The programmers make the application available to themselves using an uncommon
port along with an ID and password only they know.
Which of the following is this an example of?