Which of the following is described as an attack agains…
Which of the following is described as an attack against an application using a malicious file?
Which of the following is this an example of?
Users at a company report that a popular news website keeps taking them to a web page with derogatory
content.
Which of the following is this an example of?
Which of the following attacks has taken place?
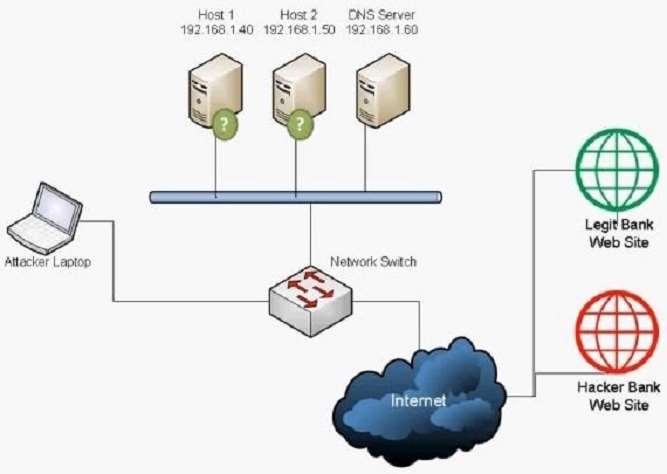
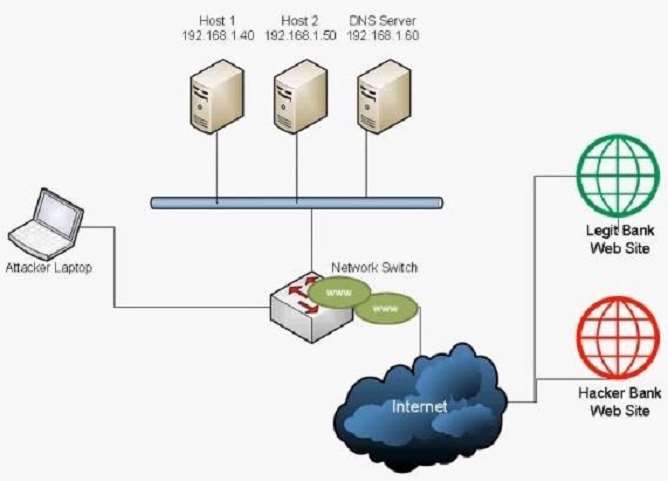
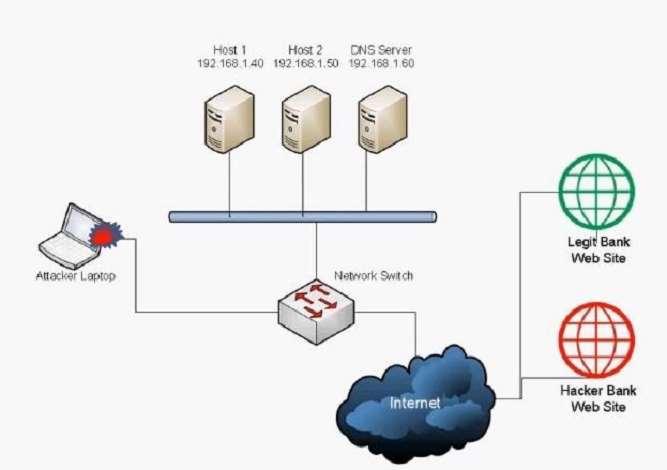
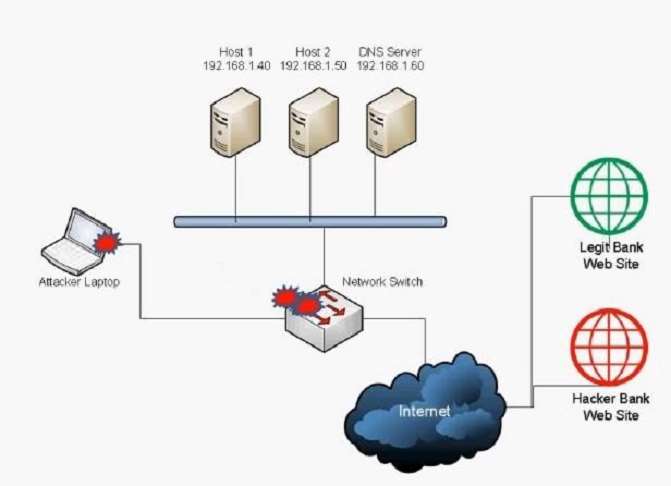
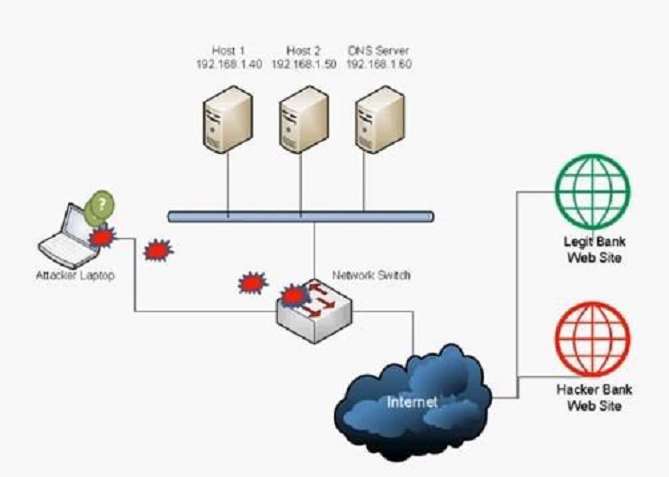
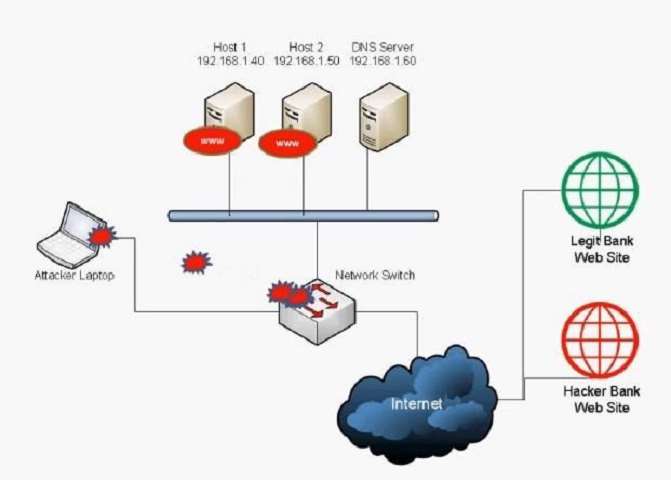
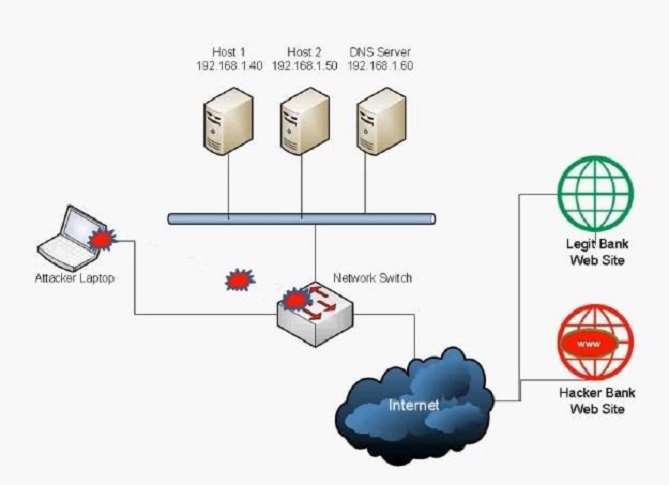
A user has unknowingly gone to a fraudulent site. The security analyst notices the following system change on
the user’s host:
Old `hosts’ file:
127.0.0.1 localhost
New `hosts’ file:
127.0.0.1 localhost
5.5.5.5 www.comptia.com
Which of the following attacks has taken place?
Which of the following controls could they implement to…
A company’s employees were victims of a spear phishing campaign impersonating the CEO. The company
would now like to implement a solution to improve the overall security posture by assuring their employees that
email originated from the CEO. Which of the following controls could they implement to BEST meet this goal?
Which of the following attack types is this?
Purchasing receives an automated phone call from a bank asking to input and verify credit card information.
The phone number displayed on the caller ID matches the bank. Which of the following attack types is this?
Which of the following attacks is being described?
Jane, an individual, has recently been calling various financial offices pretending to be another person to gain
financial information. Which of the following attacks is being described?
Which of the following attacks is this an example of?
A security administrator notices large amounts of traffic within the network heading out to an external website.
The website seems to be a fake bank site with a phone number that when called, asks for sensitive information.
After further investigation, the security administrator notices that a fake link was sent to several users.
Which of the following attacks is this an example of?
Which of the following is this an example of?
Several users’ computers are no longer responding normally and sending out spam email to the users’ entire
contact list.
Which of the following is this an example of?
Which of the following is this an example of?
Mike, a user, states that he is receiving several unwanted emails about home loans.
Which of the following is this an example of?