A way to assure data at-rest is secure even in the even…
A way to assure data at-rest is secure even in the event of loss or theft is to use:
Which of the following topologies would the engineer im…
A network engineer needs to set up a topology that will not fail if there is an outage on a single piece of the topology. However, the computers need to wait to talk on
the network to avoid congestions. Which of the following topologies would the engineer implement?
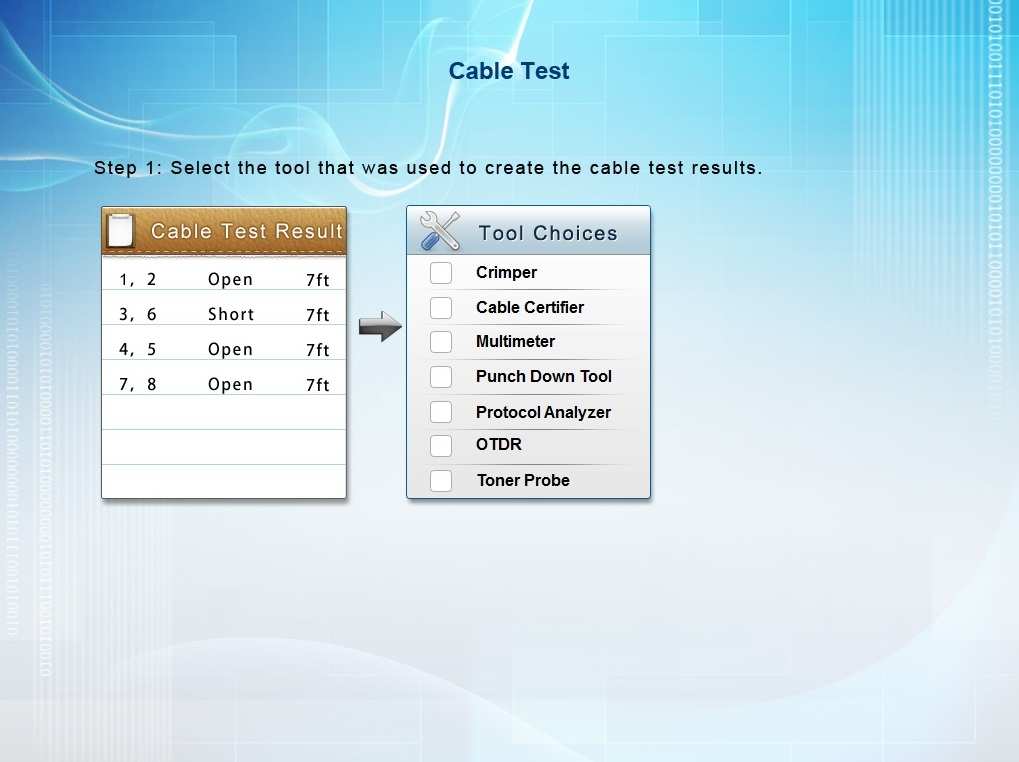
You have been tasked with testing a CAT5e cable.
CORRECT TEXT
SIMULATION
You have been tasked with testing a CAT5e cable. A summary of the test results can be found on the screen.
Step 1: Select the tool that was used to create the cable test results.
Step 2: Interpret the test results and select the option that explains the results. After you are done with your analysis, click the ‘Submit Cable Test Analysis’ button.
Which of the following controls can be implemented toge…
Which of the following controls can be implemented together to prevent data loss in the event of theft of a mobile device storing sensitive information? (Select
TWO).
Which of the following Ethernet standards could the tec…
A network technician must utilize multimode fiber to uplink a new networking device. Which of the following Ethernet standards could the technician utilize? (Select
TWO).
Which of the following can be used on a smartphone to B…
Which of the following can be used on a smartphone to BEST protect against sensitive data loss if the device is stolen? (Select TWO).
which of the following types of cabling?
An F-connector is used on which of the following types of cabling?
Which of the following can a security administrator imp…
Which of the following can a security administrator implement on mobile devices that will help prevent unwanted people from viewing the data if the device is left
unattended?
Which of the following connection types is used to term…
Which of the following connection types is used to terminate DS3 connections in a telecommunications facility?
Which of the following practices is used to mitigate a …
Which of the following practices is used to mitigate a known security vulnerability?