Which of the following authentication methods is MOST l…
A system administrator is using a packet sniffer to troubleshoot remote authentication. The administrator detects a device trying to communicate to TCP port 49.
Which of the following authentication methods is MOST likely being attempted?
Which of the following would be the result of this action?
A network technician is troubleshooting a problem at a remote site. It has been determined that the connection from router A to router B is down. The technician at
the remote site re-terminates the CAT5 cable that connects the two routers as a straight through cable. The cable is then tested and is plugged into the correct
interface. Which of the following would be the result of this action?
Which of the following is mainly used for remote access…
Which of the following is mainly used for remote access into the network?
which the malicious user gained access to the switches?
Two weeks after installation, a network technician is now unable to log onto any of the newly installed company switches. The technician suspects that a malicious
user may have changed the switches’ settings before they were installed in secure areas. Which of the following is the MOST likely way in which the malicious user
gained access to the switches?
Which of the following is the BEST service for Ann to i…
Ann has taken over as the new head of the IT department. One of her first assignments was to implement AAA in preparation for the company’s new
telecommuting policy. When she takes inventory of the organizations existing network infrastructure, she makes note that it is a mix of several different vendors.
Ann knows she needs a method of secure centralized access to the company’s network resources. Which of the following is the BEST service for Ann to
implement?
Which of the following will resolve the issue?
A network administrator recently installed a web proxy server at a customer’s site. The following week, a system administrator replaced the DNS server overnight.
The next day, customers began having issues accessing public websites. Which of the following will resolve the issue?
Which of the following relies on the use of shared secr…
Which of the following relies on the use of shared secrets to protect communication?
Which of the following is MOST likely the cause of the …
A PC technician has installed a new network printer that was preconfigured with the correct static IP address, subnet mask, and default gateway. The printer was
installed with a new cable and appears to have link activity, but the printer will not respond to any network communication attempts. Which of the following is MOST
likely the cause of the problem?
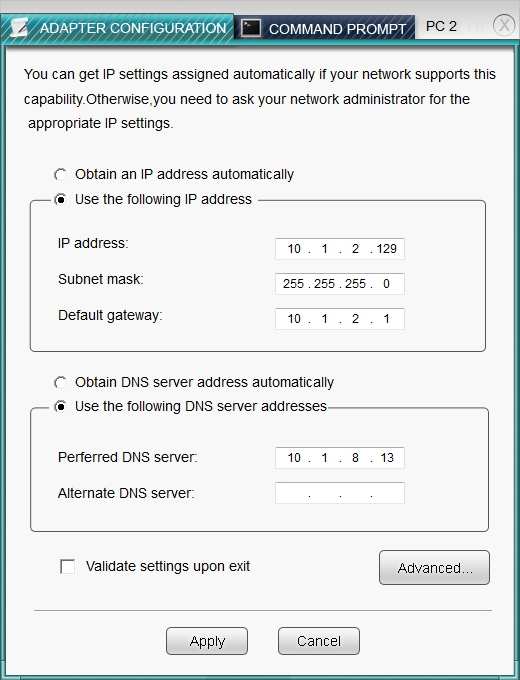
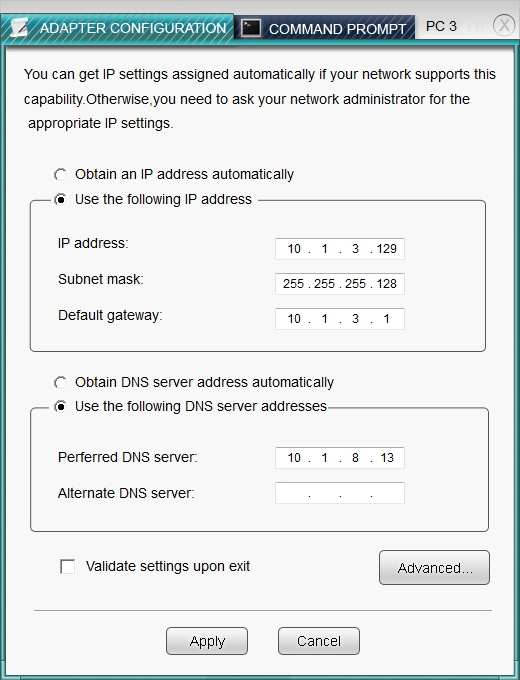
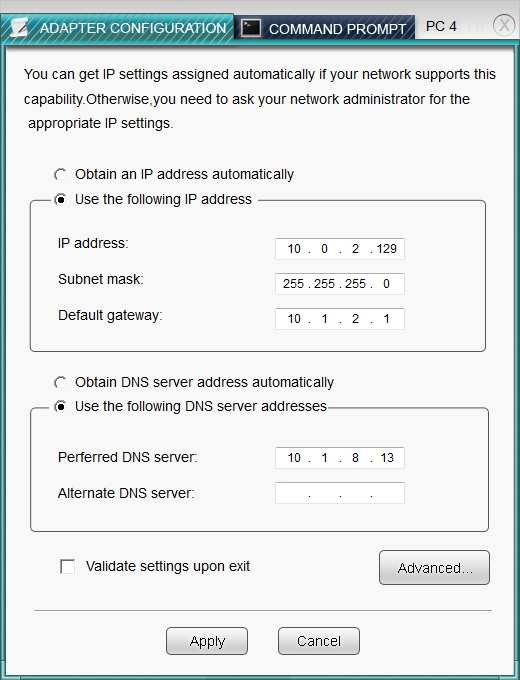
After recent changes to the pictured network, several users are unable…
CORRECT TEXT
SIMULATION
After recent changes to the pictured network, several users are unable to access the servers. Only PC1, PC2, PC3, and PC4 are clickable and will give you access
to the command prompt and the adapter configuration tabs.
Instructions: Verify the settings by using the command prompt, after making any system changes. Next, restore connectivity by making the appropriate changes to
the infrastructure. When you have completed these steps, select the Done button to submit.
Which of the following types of security services are u…
Which of the following types of security services are used to support authentication for remote users and devices?