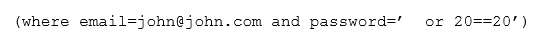Which of the following if the MOST likely explanation f…
A system administrator recently deployed and verified the installation of a critical patch issued by the company’s primary OS vendor. This patch was supposed to remedy a vulnerability that would allow an adversary to remotely execute code from over the network. However, the administrator just ran a vulnerability assessment of networked systems, and each of them still reported having the same vulnerability. Which of the following if the
MOST likely explanation for this?
Which of the following frameworks would BEST support th…
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team. Which of the following frameworks would BEST support the program? (Select two.)
Which of the following threats did the engineer MOST li…
A reverse engineer was analyzing malware found on a retailer’s network and found code extracting track data in memory. Which of the following threats did the engineer MOST likely uncover?
Which of the following documents should include these d…
A company that is hiring a penetration tester wants to exclude social engineering from the list of authorized activities. Which of the following documents should include these details?
Which of the following attacks is occurring?
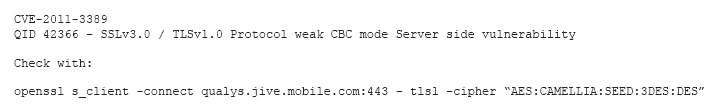
Which of the following is the BEST response?
A security audit revealed that port 389 has been used instead of 636 when connecting to LDAP for the authentication of users. The remediation recommended by the audit was to switch the port to 636 wherever technically possible. Which of the following is the BEST response?
what this code has done on the network?
A cybersecurity analyst has received the laptop of a user who recently left the company. The analyst types
‘history’ into the prompt, and sees this line of code in the latest bash history: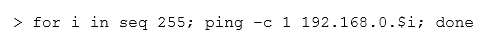
This concerns the analyst because this subnet should not be known to users within the company. Which of the following describes what this code has done on the network?
Which of the following can be implemented to maintain t…
A company has recently launched a new billing invoice website for a few key vendors. The cybersecurity analyst is receiving calls that the website is performing slowly and the pages sometimes time out. The analyst notices the website is receiving millions of requests, causing the service to become unavailable. Which of the following can be implemented to maintain the availability of the website?
Which of the following should the analyst recommend to …
A security analyst is adding input to the incident response communication plan. A company officer has suggested that if a data breach occurs, only affected parties should be notified to keep an incident from becoming a media headline. Which of the following should the analyst recommend to the company officer?