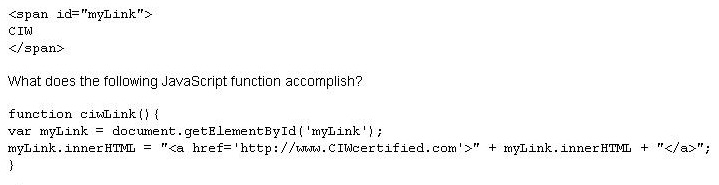
Which type of attack uses a database or databases to guess a password in order to gain access to a computer sy
Which type of attack uses a database or databases to guess a password in order to gain access to
a computer system?
what is the value of @ARGV?
Consider the following command:
perl runme.pl arg1 arg2 arg3
Given this command issued on the command line, what is the value of @ARGV?
Which choice best defines Return On Investment (ROI)?
Which choice best defines Return On Investment (ROI)?
which exception should be thrown to the client?
If an ejbFindByPrimaryKey() method cannot locate a particular record, which exception should be
thrown to the client?
Which method is not effective for protecting server scripts?
Which method is not effective for protecting server scripts?
Which of the following can you use to ensure that the window is displayed in the proper location?
You have decided that using a pop-up window is appropriate in a particular situation. Which of the
following can you use to ensure that the window is displayed in the proper location?
What problem has occurred?
Several SQL operations are performed by User 1 to access the Fee information for Bowling in the
Act_Fee relation (shown in the exhibit).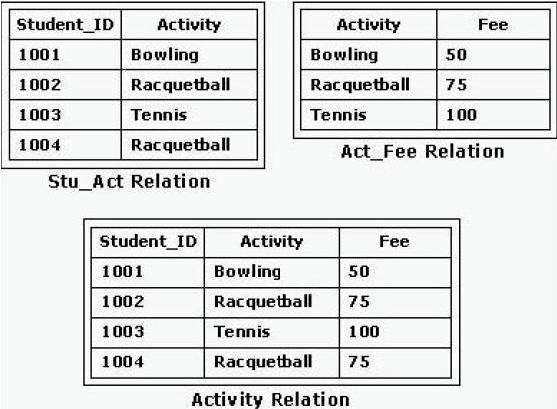
The first access returns a fee of 50. An unrelated SQL operation by another user updates the Bowling fee to 60. The second access by User 1 returns a fee of 60. What problem has occurred?
_________ is the process of creating new copies of an object
_________ is the process of creating new copies of an object
Which of the following most efficiently ensures that requests are properly processed by this second Web server
You want to configure a second Web site on a server. Which of the following most efficiently
ensures that requests are properly processed by this second Web server for customers around the
world?