Which of the following code examples will validate as XHTML 1.0 Transitional?
You have been asked to insert an image named kayak.jpg in a Web page. Which of the following
code examples will validate as XHTML 1.0 Transitional?
What consequence would occur if the tuple for Student_ID 1001 were removed?
The exhibit shows a table called Activity Relation that relates a unique student identification
number with a sports activity and a fee for participating in that activity. A student can participate in
only one activity. The key for the relation is Student_ID. What consequence would occur if the tuple for Student_ID 1001 were removed?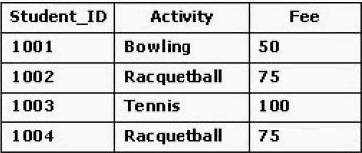
_______ represent various attributes of an object, such as height, color, font size, sentence length, and so f
_______ represent various attributes of an object, such as height, color, font size, sentence
length, and so forth.
This ability to remember the details of an order is known as:
The details of an e-commerce site order can be kept in memory, stored on the visitor’s computer
or stored on the Web server. This ability to remember the details of an order is known as:
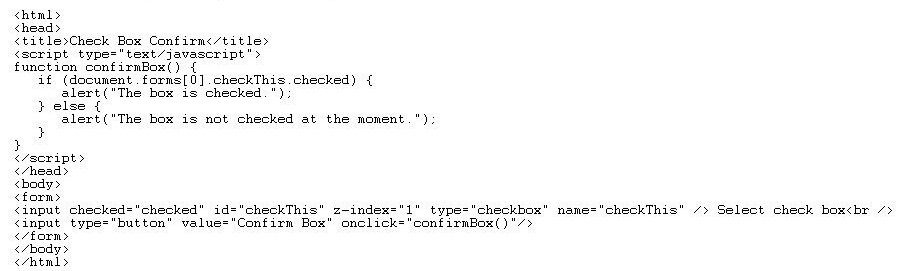
Which checkbox property was used by JavaScript?
Which Internet control message protocol (ICMPv6) message type would you receive if the Hop limit field reached
Which Internet control message protocol (ICMPv6) message type would you receive if the Hop
limit field reached zero?
Which choice lists the elements that are necessary for a CGI session?
Which choice lists the elements that are necessary for a CGI session?
Which parameters can Seamus use to return only the information he wants?
Seamus is looking for information on his network card. He executes the DMSG
command in Linux. But the output fails several text screens. Which parameters can
Seamus use to return only the information he wants?
Which type of attack is most likely to occur in this situation?
An e-mail client on an end user’s desktop has just logged on to a remote server using POP3. The
login was not encrypted. Which type of attack is most likely to occur in this situation?
Which of the following is the primary weakness of symmetric-key encryption?
Which of the following is the primary weakness of symmetric-key encryption?