What is the most probable cause?
Winston’s computer has the IP address 192.168.23.115. Winston uses a direct connection to the
Internet, but he cannot access any resources on the Internet. What is the most probable cause?
Which statement is true of your design?
Which of the following examples of code are best suited for crossplatform design?
You are using a style sheet. Which of the following examples of code are best suited for crossplatform design?
Which SQL statement or statements would best accomplish this?
Consider the Recreation relation in the exhibit. A data operation that changes one of the tuples for
Student_ID 1003 must be performed. It is necessary to change one of the activities from
swimming to tennis. The Student_ID and Activity attributes make up the primary key for the
Recreation relation. All related information must be altered, as well. Which SQL statement or
statements would best accomplish this?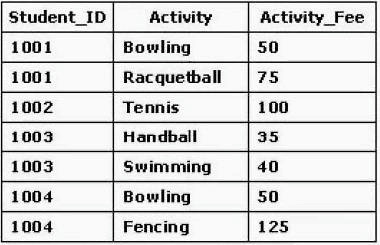
What is the term for using a single secret key to both encrypt and decrypt your data?
What is the term for using a single secret key to both encrypt and decrypt your data?
Which of the following will correctly declare the EmployeeID variable as a string data type?
Which of the following will correctly declare the EmployeeID variable as a string data type?
What is the major difference between Simple network management protocol (SNMP) and remote network monitoring (
What is the major difference between Simple network management protocol (SNMP) and remote
network monitoring (RMON)?
Which markup language describes document content instead of adding structure or formatting to document content
Which markup language describes document content instead of adding structure or formatting to
document content?
what will this command return?
Alison is testing her new web server. She executes the following command in the
telnet session:
Head/hello.http/1.0
Assuming that Alison’s is working correctly what will this command return?
Which of the following best describes a buffer overflow attack?
Which of the following best describes a buffer overflow attack?


