Which form of encryption should you use?
You have been asked to encrypt a large file using a secure encryption algorithm so you can send
it via e-mail to your supervisor. Encryption speed is important. The key will not be transmitted
across a network. Which form of encryption should you use?
Which UML diagrams can be used to show parallel or concurrent behavior?
Which UML diagrams can be used to show parallel or concurrent behavior?
which of the following image file types?
A mobile WML-enabled device is most likely to support which of the following image file types?
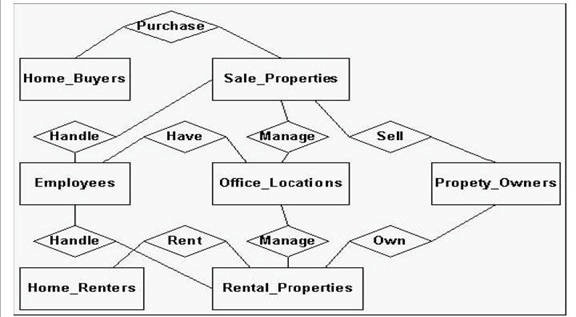
Which term best describes the diagram shown in the exhibit?
To perform at the maximum level of security, digital certificates must be:
To perform at the maximum level of security, digital certificates must be:
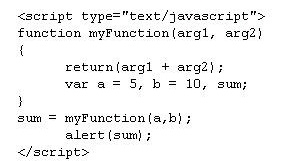
Consider the following code: Will this function generate an error?
Which of the following stages of the hacker process has this hacker completed?
An attacker has just installed a root kit on a system. Which of the following stages of the hacker
process has this hacker completed?
which all hard disk data is lost?
Which of the following is the most likely first step to enable a server to recover from a denial-ofservice attack in which all hard disk data is lost?
Which of the following should be considered by an analyst?
The requirements for a system include a large number of concurrent clients, high volume of
service requests, and guaranteed execution of sets of actions as one atomic action. Which of the
following should be considered by an analyst?
Which of the following is the best way to ensure that a servlet will only process a single request at a time?
Which of the following is the best way to ensure that a servlet will only process a single request at
a time?