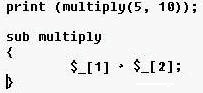What is the term for this type of scanning attack?
A malicious user has connected to your system and learned the specifics of your operating
system, including its current patch levels and the operating system name. What is the term for this
type of scanning attack?
Which choice correctly describes a benefit of asymmetric-key encryption?
You are asked about the benefits of asymmetric-key encryption. Which choice correctly describes
a benefit of asymmetric-key encryption?
What is the result of executing this program code?
what happens?
If a Web page uses both a linked style sheet and style header blocks, what happens?
Which statement correctly describes the EJBObject interface?
Which statement correctly describes the EJBObject interface?
which of the following represents the concatenation operator?
In PHP, which of the following represents the concatenation operator?
What should be done to ensure that the site meets the college’s strict accessibility policy?
A college is considering allowing podcasting on its student Web site. What should be done to
ensure that the site meets the college’s strict accessibility policy?
Which of the following best describes white-box testing of the projects software?
Your enterprise has created a database and database application. The testing phase for the
project has started. Which of the following best describes white-box testing of the projects
software?
In JavaScript terms, a sentence on a page is an example of ____________
In JavaScript terms, a sentence on a page is an example of ____________
Blogads are:
Blogads are: