Which one of the following choices best describes how to load a list of database tables into an array?
Which one of the following choices best describes how to load a list of database tables into an
array?
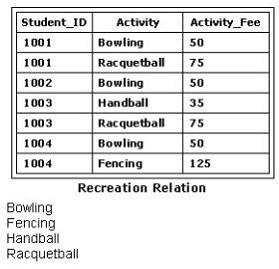
You need to apply a SQL statement to the Recreation relation that will return the following data: Which SQL
The __________ method tests for the presence and position of a certain character.
The __________ method tests for the presence and position of a certain character.
The Web server is the target of:
Yvonne has received reports that the Web server she administers has been responding slowly to
page requests, and often responds so slowly that requested pages are never received. After
reviewing the server logs, Yvonne determines that the Web server has received more than 1
billion requests sent to a nonexistent port. The Web server is the target of:
Which type of DNS server must she install?
Reiko works for an ISP where she must implement a DNS server that will host multiple company
domains. Which type of DNS server must she install?
Which of the following choices will best help Mathilda to simplify the process?
Mathilda is a Linux administrator on a large network. She does not have access to
Linux.conf. But she wants to automate the account creating process. Which of the
following choices will best help Mathilda to simplify the process?
Which of the following should be regularly backed up in a Windows system, in case a security breach occurs?
Which of the following should be regularly backed up in a Windows system, in case a security
breach occurs?
Which of the following Model and View interactions BEST satisfies the above requirements?
The following are the requirements for a Report-generation module in an application:
1.When new data is generated, the user-interface should be refreshed automatically to reflect the
latest values
2.Multiple view types are possible
Which of the following Model and View interactions BEST satisfies the above requirements?
which type of EJB is most appropriate for managing persistent information through JDBC?
According to the J2EE Blueprints, which type of EJB is most appropriate for managing persistent
information through JDBC?
What action should he take at the firewall?
Raul wants to ensure that a hacker cannot access his DNS zone files. What action should he take
at the firewall?