Which value must you increment on your primary server so that the secondary server will update its contents?
You updated your primary server with new hosts. However, you notice that the
secondary server has not updated its contents. Which value must you increment on your
primary server so that the secondary server will update its contents?
Which of the following was conducted to enable this conclusion?
After consulting with the IT department, you have determined that a particular security solution is
quite effective for protecting a particular resource, but not necessary due to the expense. Which of
the following was conducted to enable this conclusion?
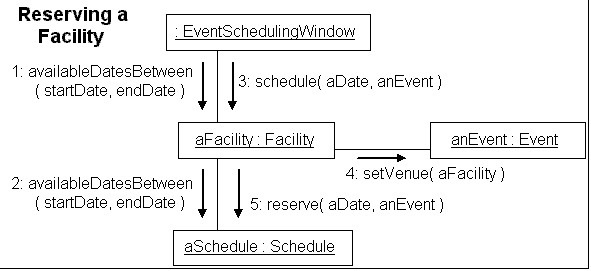
What public methods are required of the Facility class?
what order would they be notified if the application were shut down?
If four classes were instantiated in the following order, implementing the associated event listener,
in what order would they be notified if the application were shut down?
CustomConnectionManager implements HttpSessionListener
CustomerManager implements ServletContextListener
OrderManager implements HttpSessionListener
ShoppingCartManager implements HttpSessionListener
which of the following are the responsibilities of the Connection object (Choose all that apply)?
Under JDBC, which of the following are the responsibilities of the Connection
object (Choose all that apply)?
Which of the following do hackers target because it usually communicates in cleartext, and because it often ca
Which of the following do hackers target because it usually communicates in cleartext, and
because it often carries sensitive information?
What is the output of this code?
Consider the following program code:
@array = (“one”, “two”);
push(@array, “three”);
shift(@array);
unshift(@array, “four”);
pop(@array);
print($array[0]);
What is the output of this code?
Which protocol is most likely to be used when sending e-mail using the Microsoft Outlook Express client?
Which protocol is most likely to be used when sending e-mail using the Microsoft Outlook Express
client?
Which law limits liability and damages against the ISP, if legal action is taken against Chuy?
Chuy’s Web site is hosted by an outside hosting service. She may be posting some legally
questionable material on her site. Which law limits liability and damages against the ISP, if legal
action is taken against Chuy?