Which HTTP-EQUIV attribute value controls the page cache to the browser folder?
Which HTTP-EQUIV attribute value controls the page cache to the browser folder?
which security measure?
Subject, Public Key, Validity Period, Issuer, Other, and Third-Party Signature are all typical fields
for which security measure?
Which one of the following variables is used if no variable was specified in a pattern match, substitution ope
Which one of the following variables is used if no variable was specified in a pattern match,
substitution operator or print statement?
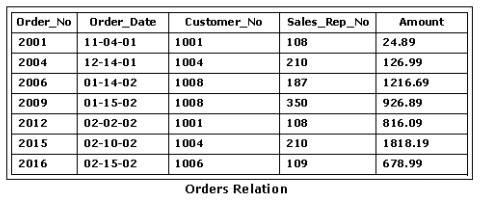
Which of the following SQL statements would return all complete tuples for order dates in 2002, arranged by am
_________ is used to associate an object’s name with the object’s properties or methods.
_________ is used to associate an object’s name with the object’s properties or methods.
Which of the following describes a root certificate authority (CA)?
Which of the following describes a root certificate authority (CA)?
Which protocol provides an encapsulation method for sending IP packets over a serial link?
Which protocol provides an encapsulation method for sending IP packets over a serial link?
What can Jeanne do to minimize customer impact of this oversight?
Jeanne is the administrator of a very large e-commerce site. She notices that the site still
contains many hypertext links to pages that were deleted from the site. What can Jeanne
do to minimize customer impact of this oversight?
What is the difference between a brute-force attack and a dictionary attack?
What is the difference between a brute-force attack and a dictionary attack?
To show where components and objects are physically located in a distributed system, it is BEST to use:
To show where components and objects are physically located in a distributed system, it is BEST
to use: