What color will the page background be when you apply this style?
You are creating a style sheet to format your Web pages. For the page background color,
you enter the hexadecimal code FF0000. What color will the page background be when you
apply this style?
Which device has features similar to a smartphone but usually does not have telephone capabilities?
Mobile computing has become a common necessity for both personal and business
transactions. Which device has features similar to a smartphone but usually does not have
telephone capabilities?
What is the best way to do this?
You want to restrict host access to a wireless access point. What is the best way to do this?
What is the difference between a computer virus and a worm?
What is the difference between a computer virus and a worm?
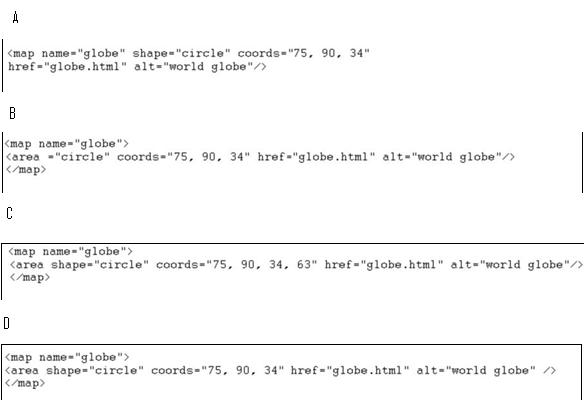
which of the following code fragments would you use?
Which attribute of the form field elements organizes information input by the user into name=value pairs?
When the user clicks the Submit Query button on a form, the browser sends the information
entered in the form to the Web server as a raw text string. The basic element of a raw text
string is a name=value pair. A CGI script parses and formats the raw text string into a
human-readable format. Which attribute of the form field elements organizes information
input by the user into name=value pairs?
This business model is commonly referred to as:
A paradigm shift has occurred in the way that small businesses use software applications.
Companies increasingly choose hosted solutions with a monthly subscription fee and
outsourced system maintenance, instead of purchasing software and hardware that must be
maintained by internal resources. This business model is commonly referred to as:
What can SuperBank request to protect its data from security threats?
SuperBank is considering a cloud service from Local Data Center, Inc., to support the
bank’s expanding needs. SuperBank’s managers are concerned about security. What can
SuperBank request to protect its data from security threats?
Which organization is responsible for managing domain names so that each one is unique, and (once regist
Which organization is responsible for managing domain names so that each one is unique,
and (once registered) cannot be used by an unauthorized individual or organization?
Which is the best approach?
A friend just sent you a link to a Facebook page with information that you find very useful.
You want to be able to recall the site in the future from your desktop computer, or from your
mobile device while away from your desk. Which is the best approach?