which of the following BEST completes the interaction diagram in the Exhibits to withdraw funds from a certifi
Refer to the exhibits to answer the question.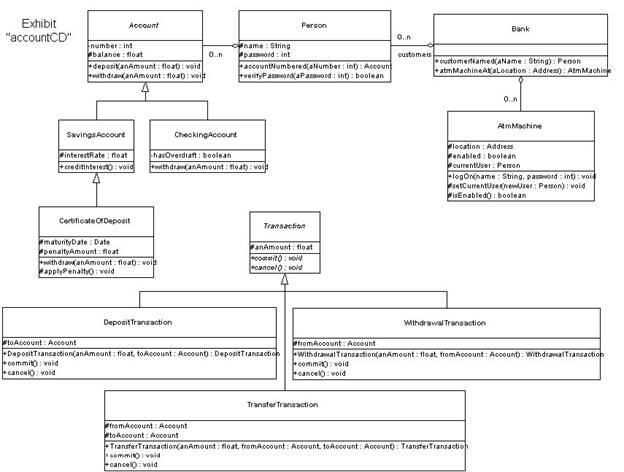
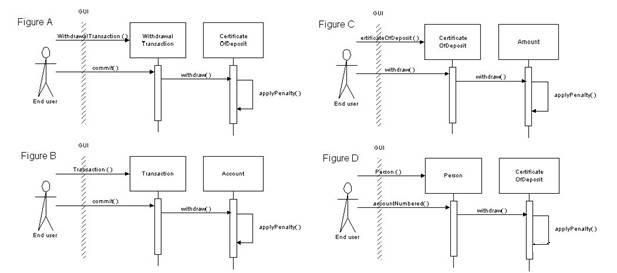
It is required to incur a penalty whenever a customer withdraws funds from a certificate of deposit
before its maturity date. Given the class diagram in the Exhibits, which of the following BEST
completes the interaction diagram in the Exhibits to withdraw funds from a certificate of deposit?
Which of the following is the best way to accomplish this?
A client is to be sent to a servlet in a separate servletContext. Which of the following is the best
way to accomplish this?
In the world of SQL relational database, a timestamp usually comprises of (choose all that apply.
In the world of SQL relational database, a timestamp usually comprises of (choose
all that apply.
what should you change to help provide security?
When setting up Microsoft Internet Information Server (IIS) in either Windows NT or Windows
2000, what should you change to help provide security?
A circuit-level gateway is one type of:
A circuit-level gateway is one type of:
which of the following evaluates as false?
Assuming $a = 2, which of the following evaluates as false?
Why He tests the image and finds that only one hyperlink works?
Liam is instructed to create a visually appealing bitmap image for the home page that links to all
the other pages. He tests the image and finds that only one hyperlink works. Why?
What is wrong with this VBScript code?
Consider the following VBScript code:
<P><FONT COLOR=”crimson” FACE=”Arial” SIZE=”4″ >Hi </FONT></P>
<SCRIPT>
<!-coloredfront.style.color = “ourcolor”
–>
</SCRIPT>
<SCRIPT TYPE=”text/vbscript”>
Sub coloredfont_onmouseover ()
coloredfont.style.color =”Green”
Sub
Sub coloredfont_onmouseou ()
coloredfont.style.color = “crimson”
END Sub
</SCRIPT>
What is wrong with this VBScript code?
This type of attack is known as a:
Jason is attempting to gain unauthorized access to a corporate server by running a program that
enters passwords from a long list of possible passwords. This type of attack is known as a:
What are the referential constraints for the relations defined in these relation definitions?
Consider the following relation definitions:
STUDENT(
Student_Number: integer NOT NULL
Name: variable length character string length 20 )
Primary Key Student_Number
HOUSING(
Housing_ID: integer NOT NULL
Student_Number: integer NOT NULL
Building: variable length character string length 25 )
Primary Key Housing_ID
Foreign Key Student_Number References STUDENT(Student_Number)
ON DELETE NO ACTION
ON UPDATE CASCADE
What are the referential constraints for the relations defined in these relation definitions?

