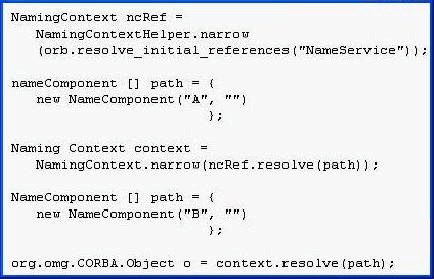
What is the purpose of this code fragment?
Which one of the following choices lists the four steps of interaction with a database?
Which one of the following choices lists the four steps of interaction with a database?
Which area of database security involves maintaining access to enterprise data?
Which area of database security involves maintaining access to enterprise data?
VBScript was the first scripting language developed for Webpage design.
VBScript was the first scripting language developed for Webpage design.
What security protocol typically allows Web-based applications to pass data securely by providing an encrypted
What security protocol typically allows Web-based applications to pass data securely by providing
an encrypted channel?
What is a typical length of IPv6 header?
What is a typical length of IPv6 header?
Which markup language describes document content instead of adding structure or formatting to document content
Which markup language describes document content instead of adding structure or formatting to
document content?
Which command can Brandy execute to discover how many hops exist form the users system to the target host syst
Brandy is a Linux administrator. She learns from a user that it takes unusually long time
to receive response from another host system. Which command can Brandy execute to
discover how many hops exist form the users system to the target host system?
Which port allows a user to access it without authentication?
Which port allows a user to access it without authentication?
What is the primary strength of symmetric-key encryption?
What is the primary strength of symmetric-key encryption?