Which of the following is most likely to protect the availability component of the CIA triad? (Select the best answer.)
A. data encryption
B. an IPS
C. a virus scanner
D. a VPN
Explanation:
Of the available choices, an Intrusion Prevention System (IPS) is most likely to protect the availability component of the confidentiality, integrity, availability (CIA) triad. The availability component of the CIA triad ensures the protection of systems against unplanned downtime as a result of security breaches. For example, a Distributed Denial of Service (DDoS) attack is a security threat that attacks availability. An IPS can help protect availability by ensuring that attacks and threats are detected and intercepted before they have a chance to cause harm.
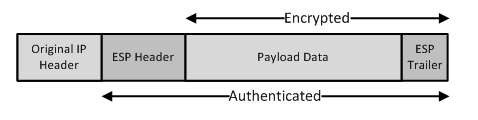
Data encryption and a virtual private network (VPN) protect confidentiality, not availability. The confidentiality component of the CIA triad ensures that transmitted data cannot be read by an unauthorized party if the data is intercepted before it reaches its destination. IP Security (IPSec), which is a security protocol often used in VPNs, can use either Advanced Encryption Standard (AES) or Data Encryption Standard (DES) to provide the confidentiality component of the CIA triad. Depending on the amount of confidentiality desired, IPSec can use AES or DES with Encapsulating Security Payload (ESP) in either transport mode or tunnel mode. In transport mode, ESP uses AES or DES to encrypt only the original payload data and the resultant ESP trailer, leaving the original IP header unencrypted. The following diagram illustrates the components of an ESP packet in transport mode:
A virus scanner protects integrity, not availability. The integrity component of the CIA triad ensures that unauthorized parties have not modified data as it was transmitted over the network. Data integrity can also be provided by using algorithms such as Message Digest 5 (MD5) or Secure Hash Algorithm (SHA) to produce checksums on each end of a connection. If the data generates the same checksum value on each end of the connection, the data was not modified in transit.
Reference:
Cisco: How to Secure Your Business (PDF)