which IPsecprotected traffic could be forwarded?
While configuring a crypto map, which command will be used to specify the peer to which IPsecprotected traffic could be forwarded?
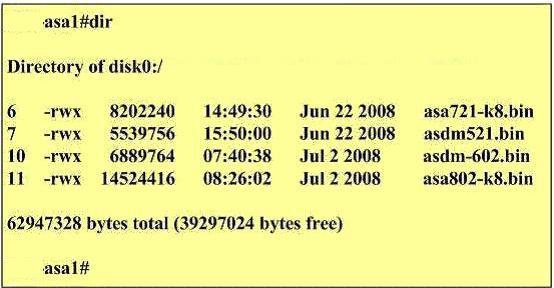
Which three commands can verify that the boot image is asa802-k8.bin according to the exhibit?
Which feature prevents ARP spoofing?
Which feature prevents ARP spoofing?
Which two statements about the downloadable ACL feature of the security appliance are correct?
Which two statements about the downloadable ACL feature of the security appliance are correct?
(Choose two.)
What is the purpose of the url-list command in global configuration mode?
What is the purpose of the url-list command in global configuration mode?
Which three commands can display the contents of flash memory on the Cisco ASA adaptive security appliance?
Which three commands can display the contents of flash memory on the Cisco ASA adaptive
security appliance? (Choose three.)
What does the following command used for?
What does the following command used for?
fw1 (config)#filter activex 80 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0
Which options can a clientless SSL VPN user access from a web browser without port forwarding, smart tunnels,
Which options can a clientless SSL VPN user access from a web browser without port forwarding,
smart tunnels, or browser plug-ins?
Which three encryption algorithms will Cisco ASA security appliances use?
Which three encryption algorithms will Cisco ASA security appliances use? (Choose three.)
What traffic is permitted based on the current configuration?
You word as a network administrator. You are asked to examine the current firewall configurations
on the LA-ASA Adaptive Security Appliances using the Cisco Adaptive Security Device Manage
(ASDM) utility. You need to answer the multiple-choice questions in this simulation using the
appropriate Cisco ASDM configuration screens.
What traffic is permitted based on the current configuration?(Choose two)