What Context-Based Access Control (CBAC) command sets the maximum time that a muter running Cisco IOS will wai
What Context-Based Access Control (CBAC) command sets the maximum time that a
muter running Cisco IOS will wait for a new TCP session to reach the established state?
What are two security controls you can implement to protect your organization’s internal network from vi
What are two security controls you can implement to protect your organization’s
internal network from virus and worm outbreaks? (Choose two.)
Which two IP multicast addresses belong to the group represented by the MAC address 0x01-00-5E-15-6A-2C?
Which two IP multicast addresses belong to the group represented by the MAC address
0x01-00-5E-15-6A-2C? (Choose two).
What action can you take to prevent an amplification attack on an IPv6 network?
What action can you take to prevent an amplification attack on an IPv6 network?
Which two features are supported in CBAC on IPv6?
Which two features are supported in CBAC on IPv6? (Choose two.)
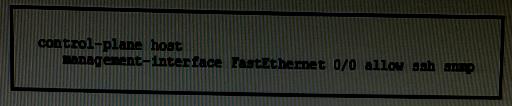
What is the effect of the given command?
What message does the TACACS+ daemon send during the AAA authentication process to request additional authenti
What message does the TACACS+ daemon send during the AAA authentication process
to request additional authentication information?
Which two statements about PIM-DM are true?
Which two statements about PIM-DM are true? (Choose two.)
How can the tail drop algorithm support traffic shaping when the queue is filled?
How can the tail drop algorithm support traffic shaping when the queue is filled?
What RADIUS attribute must the ISE server return to change the switch’s port mode to trunk?
You have configured an authenticator switch in access mode on a network configured
with NEAT. What RADIUS attribute must the ISE server return to change the switch’s
port mode to trunk?