Which three statements are true?
Which statement is true?
Which statement is true about the IPS signature shown?
which traffic can pass through a Cisco ASA that is oper…
By default, which traffic can pass through a Cisco ASA that is operating in transparent mode without explicitly allowing it using an ACL?
which MPF CLI configuration command?
On the Cisco ASA, tcp-map can be applied to a traffic class using which MPF CLI configuration command?
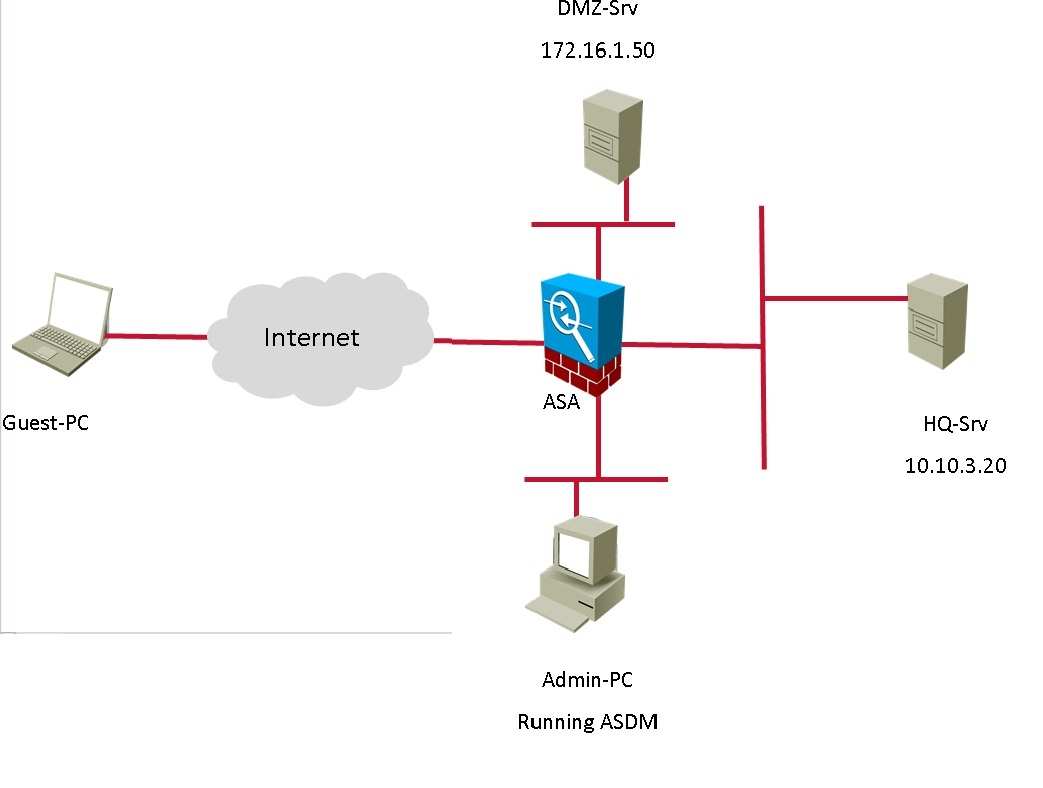
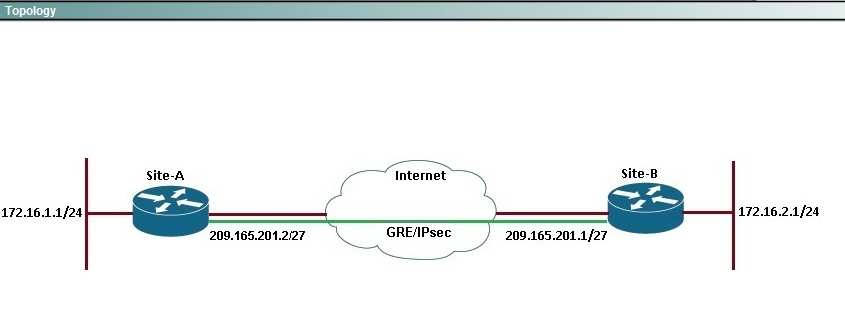
Topology:
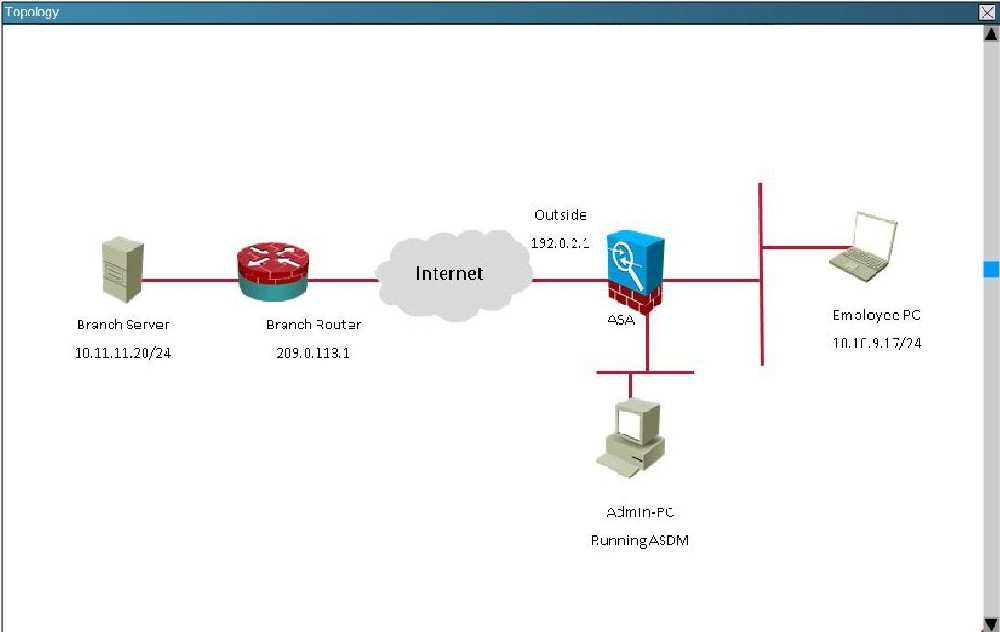
You are the network security manager for your organization. Your manager has received a request to allow an external user to access to your HQ and DM2 servers.
You are given the following connection parameters for this task.
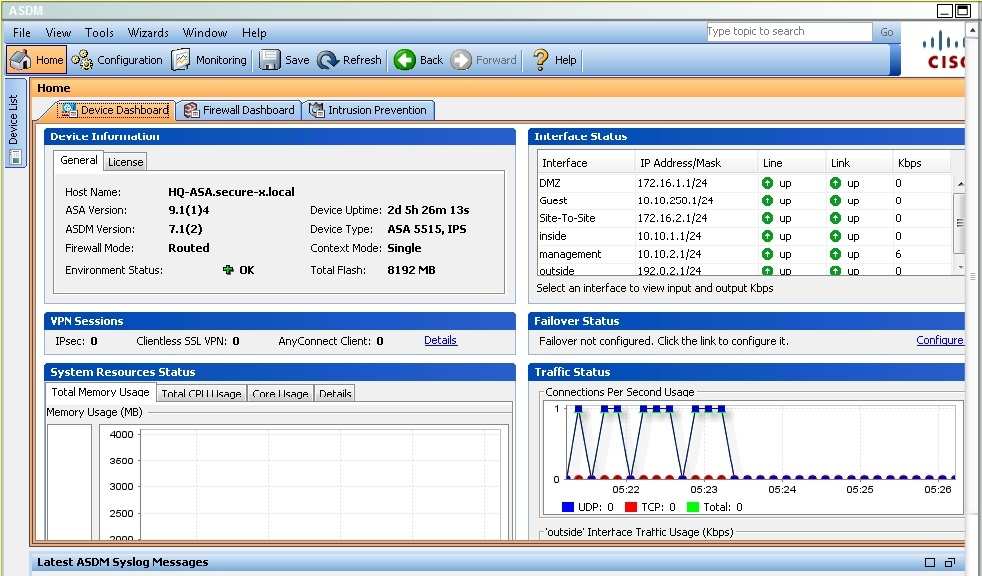
Using ASDM on the ASA, configure the parameters below and test your configuration by accessing the Guest PC. Not all AS DM screens are active for this
exercise. Also, for this exercise, all changes are automatically applied to the ASA and you will not have to click APPLY to apply the changes manually.
• Enable Clientless SSL VPN on the outside interface
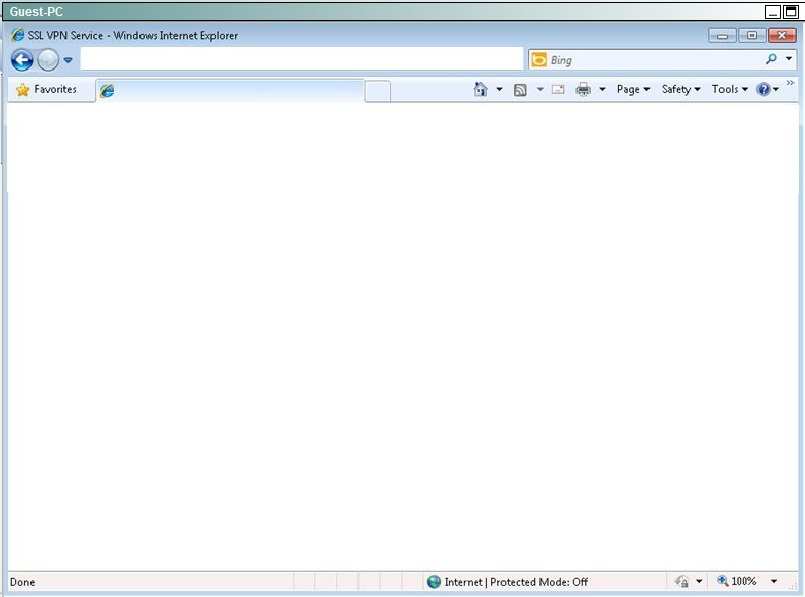
• Using the Guest PC, open an Internet Explorer window and test and verify the basic connection to the SSL VPN portal using address: https://vpn-secure-x.public
• a. You may notice a certificate error in the status bar, this can be ignored for this exercise
• b. Username: vpnuser
• c. Password: cisco123
• d. Logout of the portal once you have verified connectivity
• Configure two bookmarks with the following parameters:
• a. Bookmark List Name: MY-BOOKMARKS
• b. Use the: URL with GET or POST method
• c. Bookmark Title: HQ-Server
• i. http://10.10.3.20
• d. Bookmark Title: DMZ-Server-FTP
• i. ftp://172.16.1.50
• e. Assign the configured Bookmarks to:
• i. DfltGrpPolicy
• ii. DfltAccessPolicy
• iii. LOCAL User: vpnuser
• From the Guest PC, reconnect to the SSL VPN Portal
• Test both configured Bookmarks to ensure desired connectivity
You have completed this exercise when you have configured and successfully tested Clientless SSL VPN connectivity.
Topology:
What should you do?
Which crypto map tag is being used on the Cisco ASA?
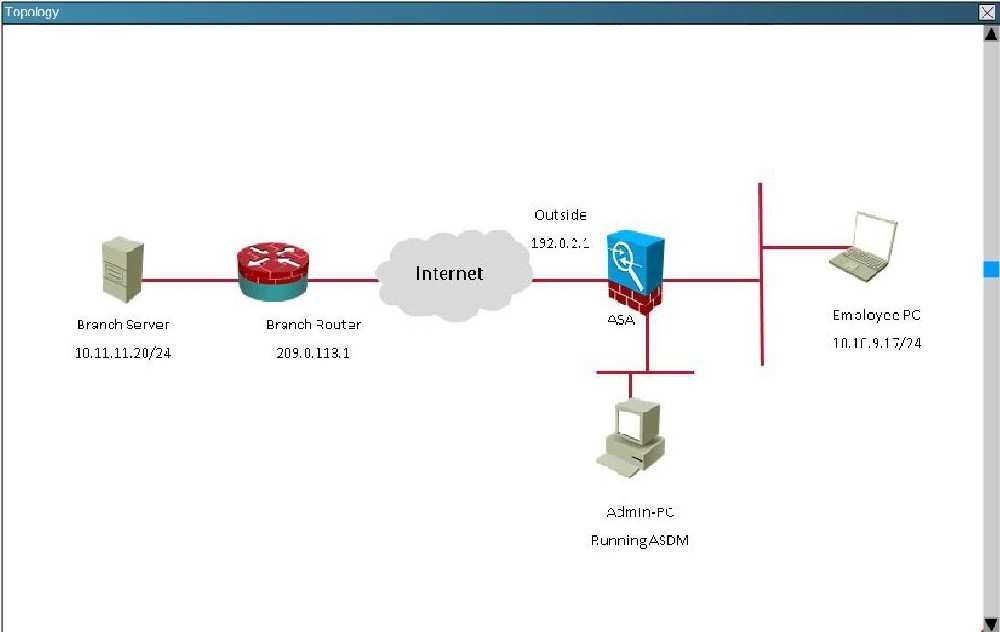
Scenario:
You are the senior network security administrator for your organization. Recently and junior engineer configured a site-to-site IPsec VPN connection between your
headquarters Cisco ASA and a remote branch office.
You are now tasked with verifying the IKEvl IPsec installation to ensure it was properly configured according to designated parameters. Using the CLI on both the
Cisco ASA and branch ISR. verify the IPsec configuration is properly configured between the two sites.
NOTE: the show running-config command cannot be used for the this exercise.
Topology:
Which crypto map tag is being used on the Cisco ASA?
what state is the IKE security association in on the Ci…
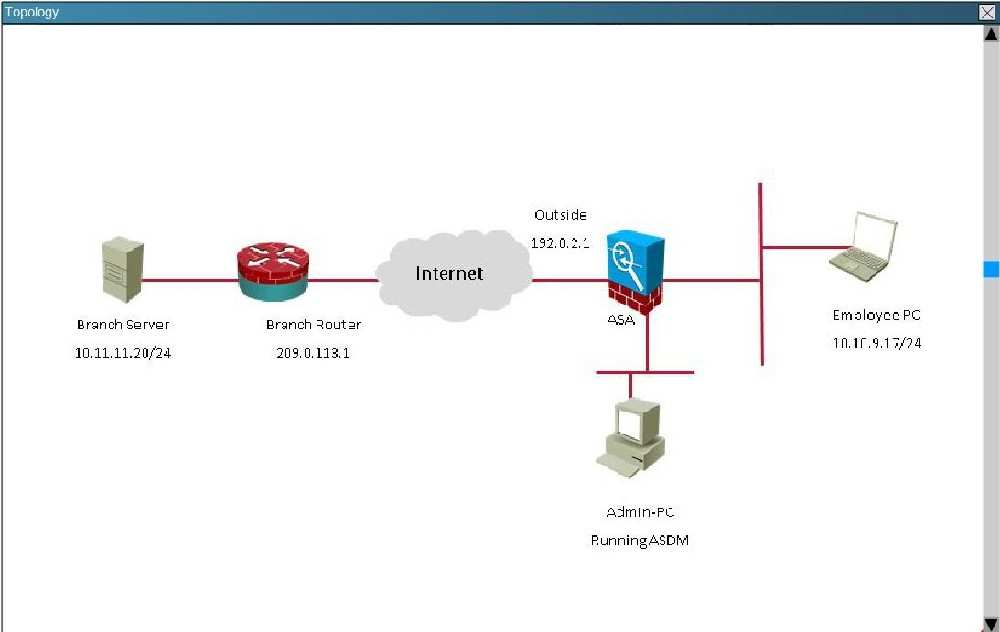
Scenario:
You are the senior network security administrator for your organization. Recently and junior engineer configured a site-to-site IPsec VPN connection between your
headquarters Cisco ASA and a remote branch office.
You are now tasked with verifying the IKEvl IPsec installation to ensure it was properly configured according to designated parameters. Using the CLI on both the
Cisco ASA and branch ISR. verify the IPsec configuration is properly configured between the two sites.
NOTE: the show running-config command cannot be used for the this exercise.
Topology:
In what state is the IKE security association in on the Cisco ASA?
Which transform set is being used on the branch ISR?
Scenario:
You are the senior network security administrator for your organization. Recently and junior engineer configured a site-to-site IPsec VPN connection between your
headquarters Cisco ASA and a remote branch office.
You are now tasked with verifying the IKEvl IPsec installation to ensure it was properly configured according to designated parameters. Using the CLI on both the
Cisco ASA and branch ISR. verify the IPsec configuration is properly configured between the two sites.
NOTE: the show running-config command cannot be used for the this exercise.
Topology:
Which transform set is being used on the branch ISR?