Why is BPDU guard an effective way to prevent an unauthorized rogue switch from altering the spanning-tree top
Why is BPDU guard an effective way to prevent an unauthorized rogue switch from altering the
spanning-tree topology of a network?
What two steps can be taken to help prevent VLAN hopping?
What two steps can be taken to help prevent VLAN hopping? (Choose two.)
how is the attacker able to gather information?
When an attacker is using switch spoofing to perform VLAN hopping, how is the attacker able to
gather information?
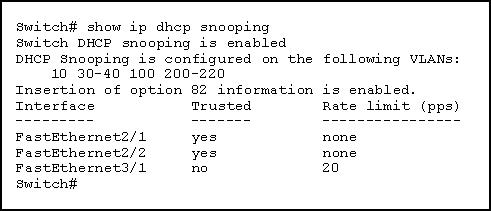
How do the switch ports handle the DHCP messages?
Which three statements about Dynamic ARP Inspection are true?
Which three statements about Dynamic ARP Inspection are true? (Choose three.)
What information should be gathered before you design the solution?
You are tasked with designing a security solution for your network. What information should be
gathered before you design the solution?
Which two components should be part of a security implementation plan?
Which two components should be part of a security implementation plan? (Choose two.)
which two pieces of information should you have obtained previously to assist in designing the solution?
When creating a network security solution, which two pieces of information should you have
obtained previously to assist in designing the solution? (Choose two.)
What action should you be prepared to take when verifying a security solution?
What action should you be prepared to take when verifying a security solution?
what is the maximum number of secure MAC addresses that should be set on the port?
When you enable port security on an interface that is also configured with a voice VLAN, what is
the maximum number of secure MAC addresses that should be set on the port?