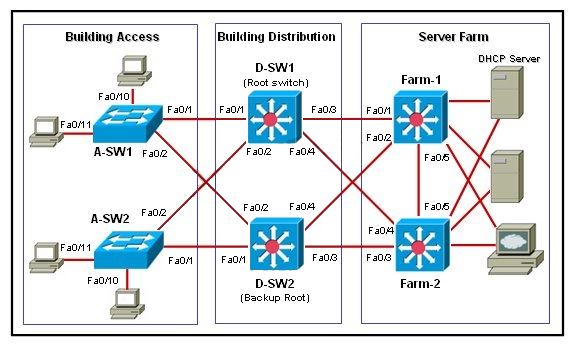
Which description correctly describes a MAC address flooding attack?
Which description correctly describes a MAC address flooding attack?
Which recommendation, if followed, would mitigate this type of attack?
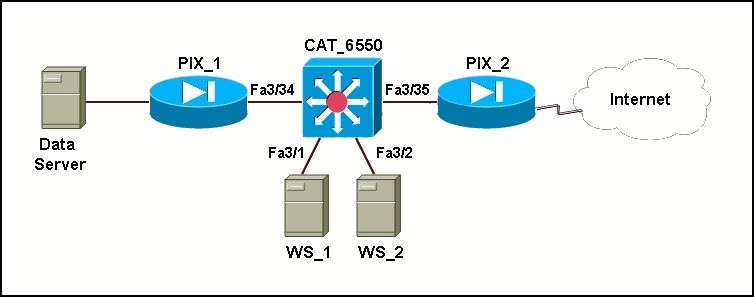
Which configuration isolates the servers from each other?
The web servers WS_1 and WS_2 need to be accessed by external and internal users. For
security reasons, the servers should not communicate with each other, although they are located
on the same subnet. However, the servers do need to communicate with a database server
located in the inside network. Which configuration isolates the servers from each other?
What does the command udld reset accomplish?
What does the command udld reset accomplish?
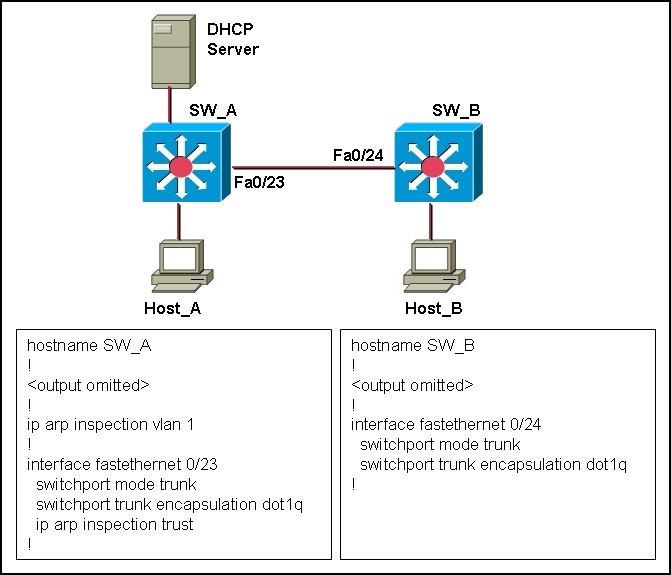
What would the outcome be if Host_B initiated an ARP spoof attack toward Host_A?
Which statement is true about Layer 2 security threats?
Which statement is true about Layer 2 security threats?
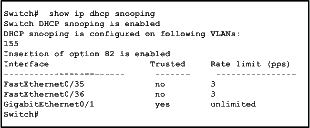
What is the purpose of this global configuration command made on R1?
On a Company switch named R1 you configure the following:
ip arp inspection vlan 10-12, 15
What is the purpose of this global configuration command made on R1?
Which two of the following statements are true?
What are two methods of mitigating MAC address flooding attacks?
What are two methods of mitigating MAC address flooding attacks? (Choose two.)
What is one method that can be used to prevent VLAN hopping?
What is one method that can be used to prevent VLAN hopping?