Which of these techniques mitigate Spanning-Tree Protocol manipulation?
Which of these techniques mitigate Spanning-Tree Protocol manipulation? (Select two.)
What is the primary identity component in a Cisco security solution?
What is the primary identity component in a Cisco security solution?
Which commands are used for basic filtering in the SAFE SMR small network campus module?
Which commands are used for basic filtering in the SAFE SMR small network campus module?
Choose two.
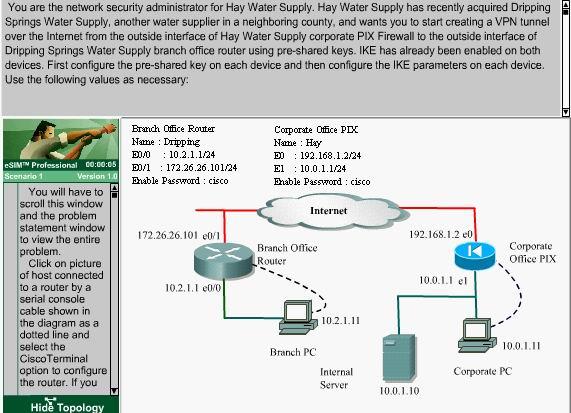
First configure the pre-shared key on each device and then configure the IKE parameters on each device.
how does the Cisco IDS appliance log events?
Using the default, how does the Cisco IDS appliance log events? Choose two.
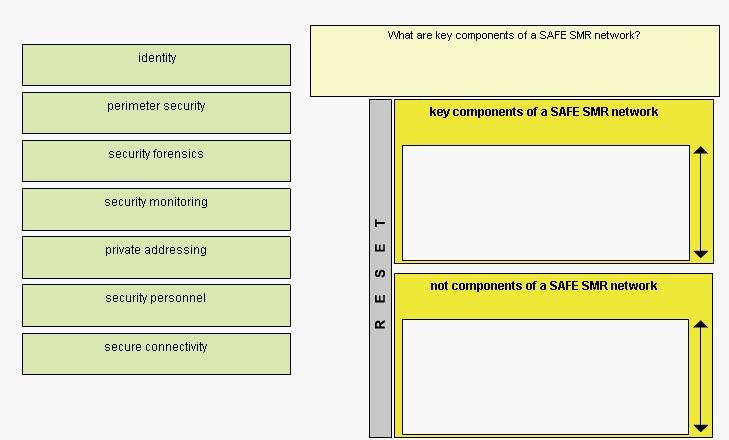
What are key components of a SAFE SMR network?
Why are all providers of Internet connectivity urged to implement the filtering described in RFC 2827?
Why are all providers of Internet connectivity urged to implement the filtering described in RFC
2827?
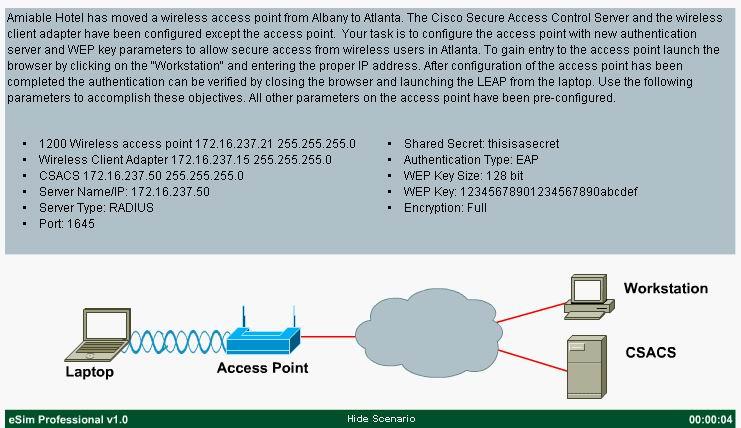
Your task is to configure the access point with new authentication server and WEP key parameters…
What signature actions can be configured on an IDS Sensor in the SAFE SMR medium network design?
What signature actions can be configured on an IDS Sensor in the SAFE SMR medium network
design? Choose two.
How are denial of service attacks mitigated in the SAFE SMR midsize network design corporate Internet module?
How are denial of service attacks mitigated in the SAFE SMR midsize network design corporate
Internet module?