Which Layer 2 protocol provides loop resolution by managing the physical paths to given network segments?
Which Layer 2 protocol provides loop resolution by managing the physical paths to given network
segments?
where should the root guard feature be deployed?
When STP mitigation features are configured, where should the root guard feature be deployed?
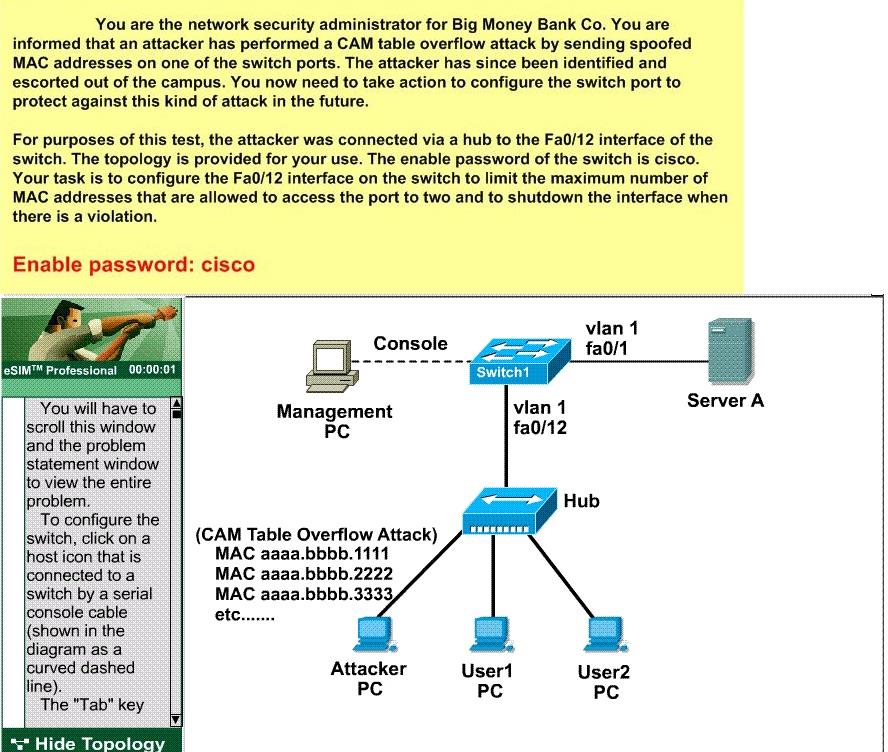
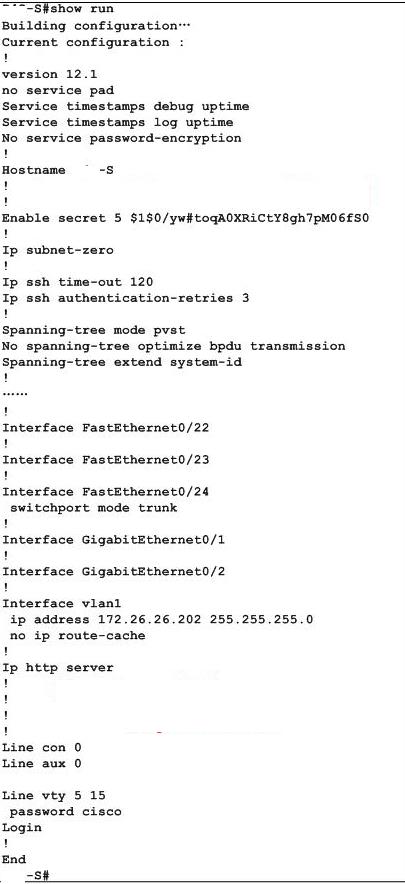
Your task is to configure the Fa0/12 interface on the switch to limit the maximum number of MAC addresses̷
Which two countermeasures can mitigate STP root bridge attacks?
Which two countermeasures can mitigate STP root bridge attacks? (Choose two.)
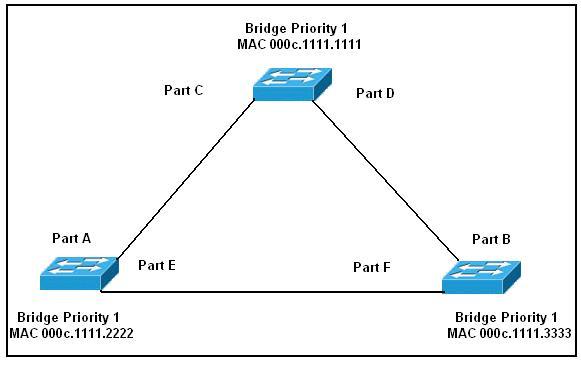
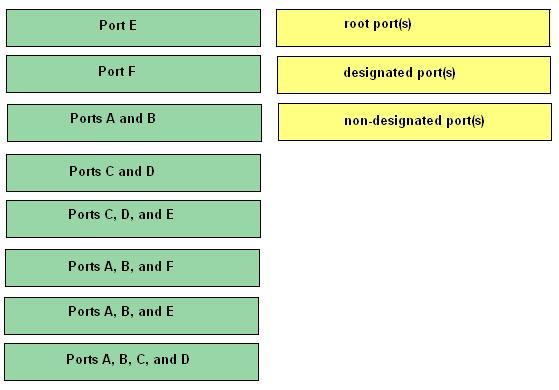
Drag the port(s) from the left and drop them on the correct STP roles on the right.
Which two countermeasures can mitigate MAC spoofing attacks?
Which two countermeasures can mitigate MAC spoofing attacks? (Choose two.)
Which statement correctly describes the function of a private VLAN?
Which statement correctly describes the function of a private VLAN?
What are two primary attack methods of VLAN hopping?
What are two primary attack methods of VLAN hopping? (Choose two.)
Which type of attack can be prevented by setting the native VLAN to an unused VLAN?
Which type of attack can be prevented by setting the native VLAN to an unused VLAN?
What is the purpose of a trunk port?
What is the purpose of a trunk port?