Which option ensures that data is not modified in transit?
Which option ensures that data is not modified in transit?
Which method is of gaining access to a system that bypasses normal security measures?
Which method is of gaining access to a system that bypasses normal security measures?
Which two actions can be configured to allow traffic to traverse an interface when zone-based security is bein
Which two actions can be configured to allow traffic to traverse an interface when zone-based
security is being employed? (Choose two.)
Which three are distinctions between asymmetric and symmetric algorithms?
Which three are distinctions between asymmetric and symmetric algorithms? (Choose all that
apply.)
Which two primary port authentication protocols are used with VSANs?
Which two primary port authentication protocols are used with VSANs? (Choose two.)
which step is performed first?
When configuring role-based CLI on a Cisco router, which step is performed first?
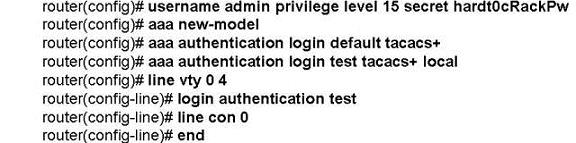
Which statement about the aaa configurations is true?
Which aaa accounting command is used to enable logging of both the start and stop records for user terminal se
Which aaa accounting command is used to enable logging of both the start and stop records for
user terminal sessions on the router?
What is a static packet-filtering firewall used for ?
What is a static packet-filtering firewall used for ?
Which characteristic is the foundation of Cisco Self-Defending Network technology?
Which characteristic is the foundation of Cisco Self-Defending Network technology?