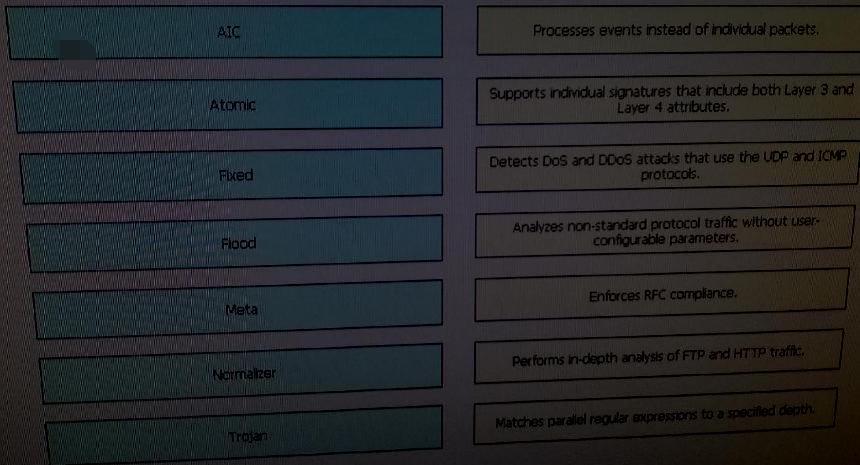
Drag each IPS Signature Engine on the left to the matching description on the right
which web policy enables failed Layer 2 authentication to fall back to WebAuth authentication with a user name
In Cisco Wireless LAN Controller (WLC) , which web policy enables failed Layer 2
authentication to fall back to WebAuth authentication with a user name and password ?
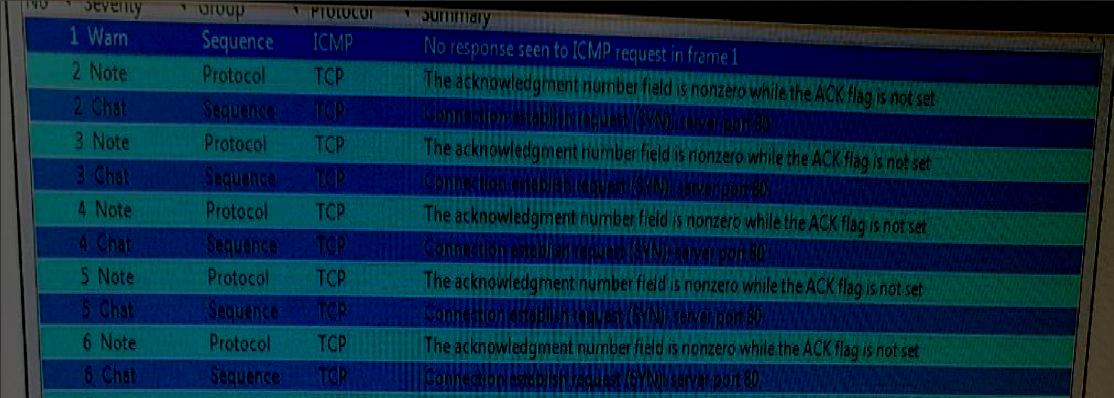
What type of attack is represented in the given Wireshark packet capture?
Which three statements about RLDP are true?
Which three statements about RLDP are true? (Choose three)
Which statement about this debug output is true?
What configuration can you perform to send the fragmented packets to the workstation at 10.0.0.2 for analysis?
Which two statements about port security are true?
Which two statements about port security are true? (Choose two.)
What are the three response types for SCEP enrollment requests?
What are the three response types for SCEP enrollment requests? (Choose three.)
What are the two most common methods that security auditors use to assess an organization’s security pro
What are the two most common methods that security auditors use to assess an
organization’s security processes? (Choose two)
What command can you use to display the number of malformed messages received by a OFICP server?
What command can you use to display the number of malformed messages received by a
OFICP server?