which two functionalities?
IKEv2 provides greater network attack resiliency against a DoS attack than IKEv1 by
utilizing which two functionalities? (Choose two)
Which two statements about the multicast addresses query messages are true?
Which two statements about the multicast addresses query messages are true? (Choose
two.)
What are four technologies that can be used to trace the source of an attack in a network environment with mul
What are four technologies that can be used to trace the source of an attack in a
network environment with multiple exit/entry points? (Choose four.)
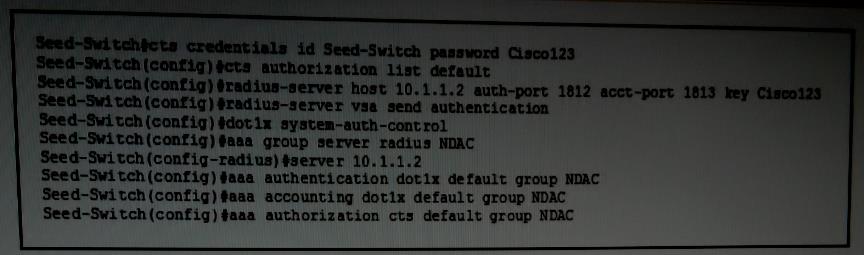
What command must you add to the seed switch’s configuration to enable secure RADIUS communication?
What Protocol provides security for datagram protocols?
What Protocol provides security for datagram protocols?
What are two effects of the given configuration?
Which two statements about the anti-replay feature are true?
Which two statements about the anti-replay feature are true? (Choose two)
What are two protocols that HTTP can use to secure sessions?
What are two protocols that HTTP can use to secure sessions? (Choose two.)
What command can you use to protect a router from TCP SYN-flooding attacks?
What command can you use to protect a router from TCP SYN-flooding attacks?
What is the effect of the Cisco Application Contra Engine (ACE) command ipv6 fragment min-mtu 1024?
What is the effect of the Cisco Application Contra Engine (ACE) command ipv6 fragment
min-mtu 1024?