What IPS risk rating allows the user to assign a risk weighting based on the relative importance of the system
What IPS risk rating allows the user to assign a risk weighting based on the relative
importance of the system involved?
What protocol format is illustrated?
What are too important guidelines to follow when implementing VTP?
What are too important guidelines to follow when implementing VTP? (Choose two.)
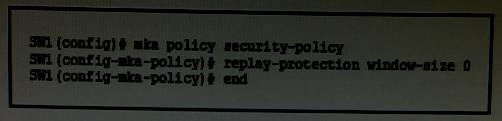
Which statement about the effect of this configuration is true?
government entities are authorized to execute and enforce the penalties for violations of the Sarbanes-Oxley (
Which two U.S. government entities are authorized to execute and enforce the
penalties for violations of the Sarbanes-Oxley (SOX) act? (Choose two)
Which ISMS provides the basis for an optional business certification logo program?
Which ISMS provides the basis for an optional business certification logo program?
What protocol does MSDP use to communicate?
What protocol does MSDP use to communicate?
Drag each step in the IPS anomaly detection configuration process on the left into…
What technique can an attacker use to obfuscate a malware application payload, allowing it to bypass standard
What technique can an attacker use to obfuscate a malware application payload,
allowing it to bypass standard security mechanisms?
Which three of these are true statements about TLS?
Which three of these are true statements about TLS? (Choose three.)