What feature can you implement on R1 to make this configuration possible?
Refer to the exhibit.
You have configured two route-map instances on R1. which passes traffic from switch 1
on both VLAN 1 and VLAN 2 You wish to ensure that * The first route-map instance
matches packets from VLAN 1 and sets the next hop to 3232:2/128. * The second routemap instance matches packets from VLAN 2 and sets the next hop to 3232:3/128. What
feature can you implement on R1 to make this configuration possible?
which two locations?
When configuring Cisco IOS Firewall CBAC operations on Cisco routers, the “inspection
rule” can be applied at which two locations? (Choose two)
what is the appropriate urgency level for remediation?
Refer to the exhibit.
You have received an advisory that your organization could be running a vulnerable
product. Using the Cisco Systems Rapid Risk Vulnerability Response Model, you
determine that * Your organization is running an affected product on a vulnerable
version of code * The vulnerable component is enabled and there is no feasible
workaround. * There is medium confidence of an attack without significant collateral
damage to the organization. According to the model, what is the appropriate urgency
level for remediation?
which three of these features?
The SSL VPN implementation on a Cisco ASA adaptive security appliance supports which
three of these features? (Choose three)
Which one of the foiling Cisco ASA adapts security appliance rule samples will send HTTP data to the AIP-SSM m
Which one of the foiling Cisco ASA adapts security appliance rule samples will send HTTP
data to the AIP-SSM module to evaluate and stop HTTP attacks?
What are two actions you can take to Protect against DDoS attacks on Cisco routers and switches?
What are two actions you can take to Protect against DDoS attacks on Cisco routers and
switches? (Choose two.)
What command must you have entered to protect the key?
What IPS form factor is best suited to handling heavy traffic between virtualized servers in a data center?
What IPS form factor is best suited to handling heavy traffic between virtualized servers
in a data center?
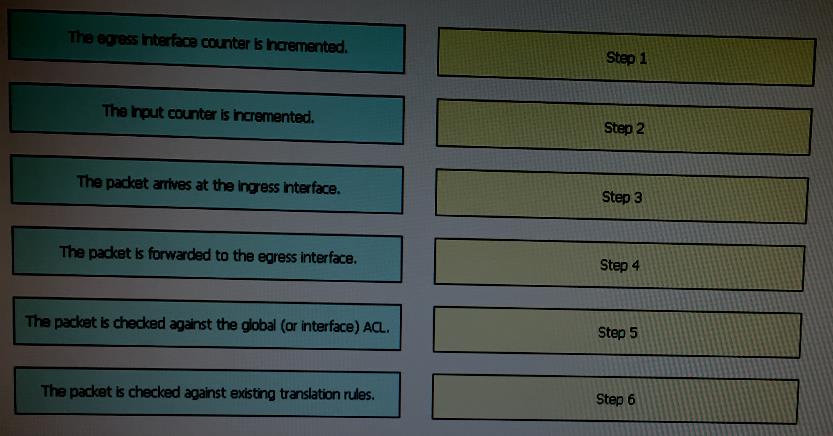
Drag and drop the step in the Cisco ASA packet processing flow on the left into…
which attribute is used to differentiate user roles?
When you configure an ASA with RADIUS authentication and authorization, which
attribute is used to differentiate user roles?