What action does a RADIUS server take when it cannot authenticate the credentials of a user?
What action does a RADIUS server take when it cannot authenticate the credentials of a
user?
Which transport mechanism is used between a RADIUS authenticator and a RADIUS authentication server?
Which transport mechanism is used between a RADIUS authenticator and a RADIUS
authentication server?
How are the username and password transmitted if a basic HTTP authentication is used?
How are the username and password transmitted if a basic HTTP authentication is used?
Which field in an HTTPS server certificate is compared to a server name in the URL?
Which field in an HTTPS server certificate is compared to a server name in the URL?
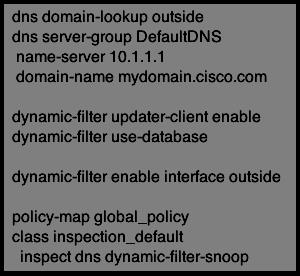
What is this configuration designed to prevent?
What does this configuration prevent?
Which two options correctly describe Remote Triggered Black Hole Filtering (RFC 5635)?
Which two options correctly describe Remote Triggered Black Hole Filtering (RFC 5635)?
(Choose two.)
which extent it should be applied?
Which standard prescribes a risk assessment to identify whether each control is
required to decrease risks and if so, to which extent it should be applied?
What is the problem with EAP-MD5?
EAP-MD5 provides one-way client authentication. The server sends the client a random
challenge. The client proves its identity by hashing the challenge and its password with
MD5. What is the problem with EAP-MD5?
which type of security threat is involved?
With ASM, sources can launch attacks by sending traffic to any groups that are
supported by an active RP. Such traffic might not reach a receiver but will reach at least
the first-hop router in the path, as well as the RP, allowing limited attacks. However, if
the attacking source knows a group to which a target receiver is listening and there are
no appropriate filters in place, then the attacking source can send traffic to that group.
This traffic is received as long as the attacking source is listening to the group.
Based on the above description, which type of security threat is involved?