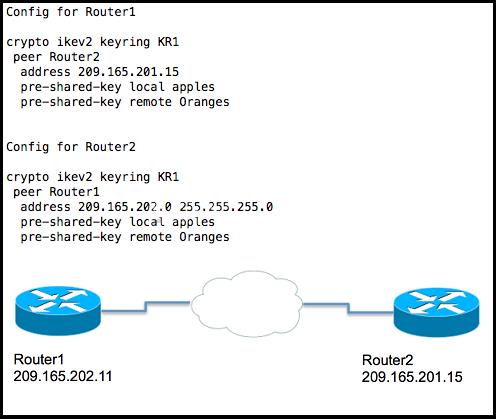
which encryption algorithm would be used to encrypt traffic?
Which of the following can be done to resolve this problem?
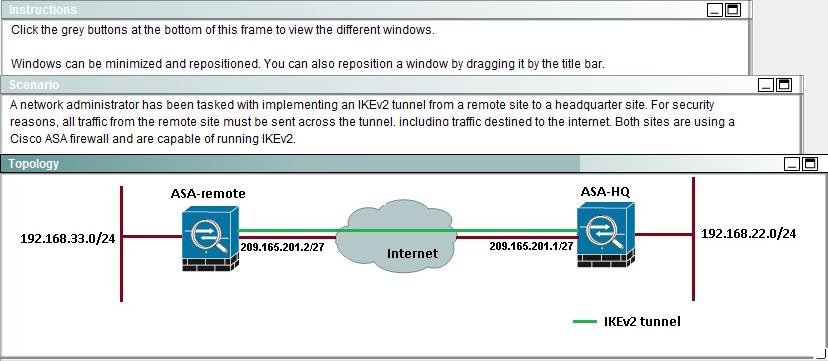
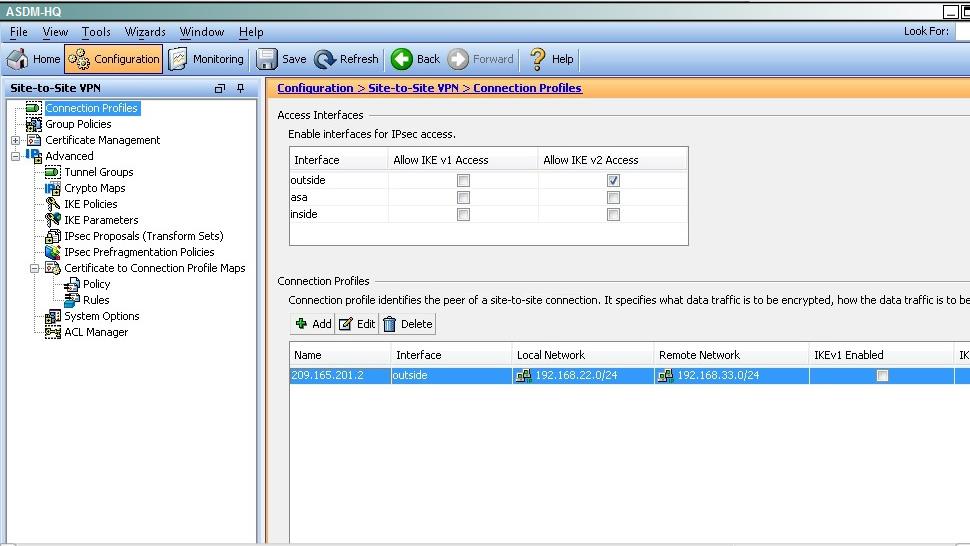
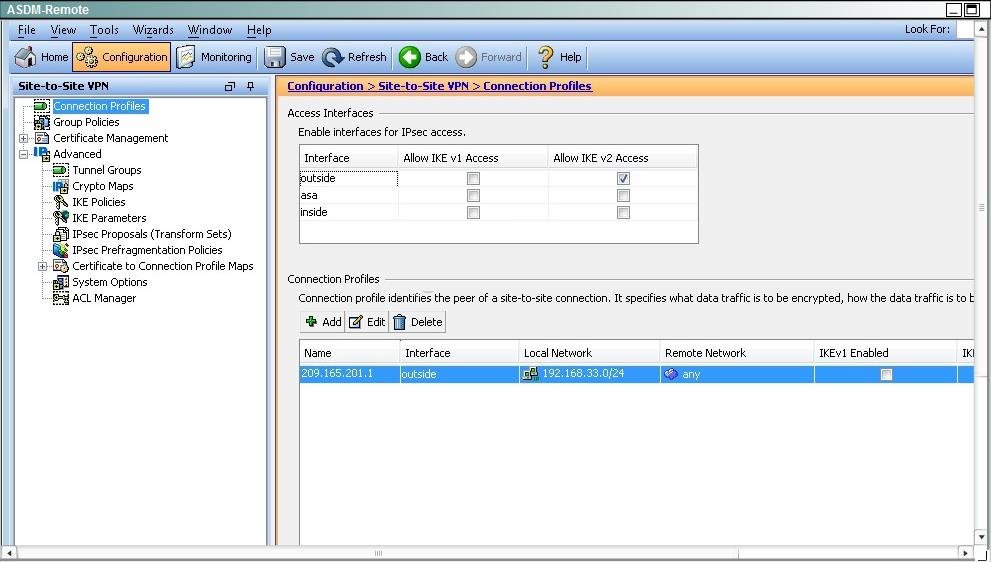
Which option shows the correct traffic selectors for the child SA on the remote ASA, when the headquarter ASA
You must use the IKEv2 configuration blocks to accomplish this task.
Which two technologies would accommodate the company’s requirement?
A custom desktop application needs to access an internal server. An administrator is tasked with
configuring the company’s SSL VPN gateway to allow remote users to work. Which two
technologies would accommodate the company’s requirement? (Choose two).
which that route originated?
A rogue static route is installed in the routing table of a Cisco FlexVPN and is causing traffic to be
blackholed. Which command should be used to identify the peer from which that route originated?