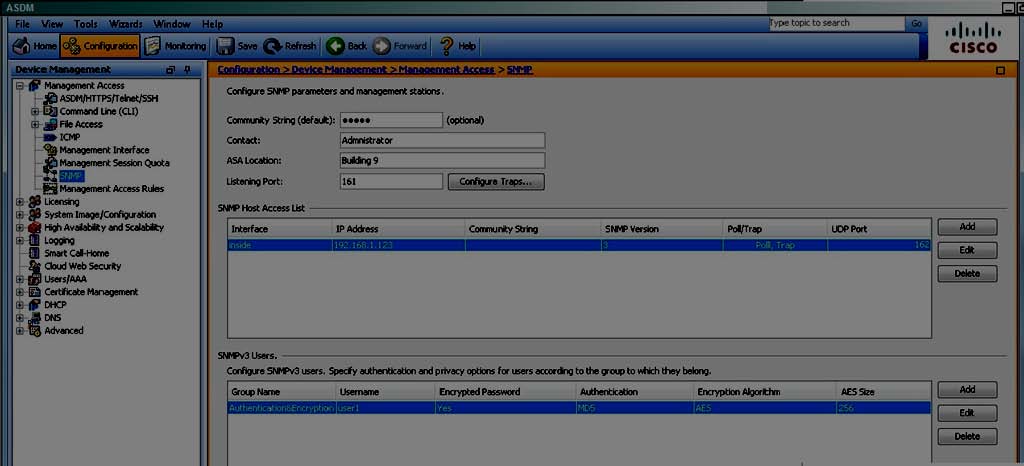
which option must you associate it?
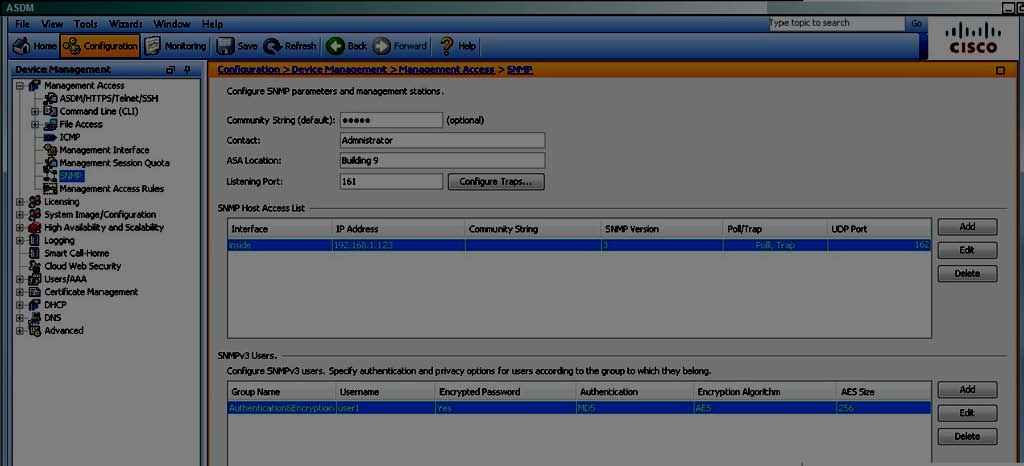
SNMP users have a specified username, a group to which the user belongs, authentication password,
encryption password, and authentication and encryption algorithms to use. The authentication
algorithm options are MD5 and SHA . The encryption algorithm options are DES, 3DES, andAES
(which is available in 128,192, and 256 versions). When you create a user, with which option must
you associate it?
which option must you configure in addition to the target IP address?
what security mechanism can prevent an attacker from gaining network topology information from CDP via a man-i
Enabling what security mechanism can prevent an attacker from gaining network topology
information from CDP via a man-in-the-middle attack?
which command is used to nest objects in a pre-existing group?
On an ASA running version 9.0, which command is used to nest objects in a pre-existing group?
Which ASA feature is used to keep track of suspected attackers who create connections to too many hosts or por
Which ASA feature is used to keep track of suspected attackers who create connections to too many
hosts or ports?
What is the default behavior of an access list on a Cisco ASA?
What is the default behavior of an access list on a Cisco ASA?
which command creates a domain for the context?
When configuring a new context on a Cisco ASA device, which command creates a domain for the
context?
Which statement describes the correct steps to enable Botnet Traffic Filtering on a Cisco ASA version 9.0 tran
Which statement describes the correct steps to enable Botnet Traffic Filtering on a Cisco ASA version
9.0 transparent-mode firewall with an active Botnet Traffic Filtering license?
Which Cisco switch technology prevents traffic on a LAN from being disrupted by a broadcast, multicast, or uni
Which Cisco switch technology prevents traffic on a LAN from being disrupted by a broadcast,
multicast, or unicast flood on a port?
Which statement describes how VLAN hopping can be avoided?
You are a security engineer at a large multinational retailer. Your Chief Information Officer recently
attended a security conference and has asked you to secure the network infrastructure from VLAN
hopping.
Which statement describes how VLAN hopping can be avoided?