Which VTP mode supports private VLANs on a switch?
Which VTP mode supports private VLANs on a switch?
Which technology can be deployed with a Cisco ASA 1000V to segregate Layer 2 access within a virtual cloud env
Which technology can be deployed with a Cisco ASA 1000V to segregate Layer 2 access within a
virtual cloud environment?
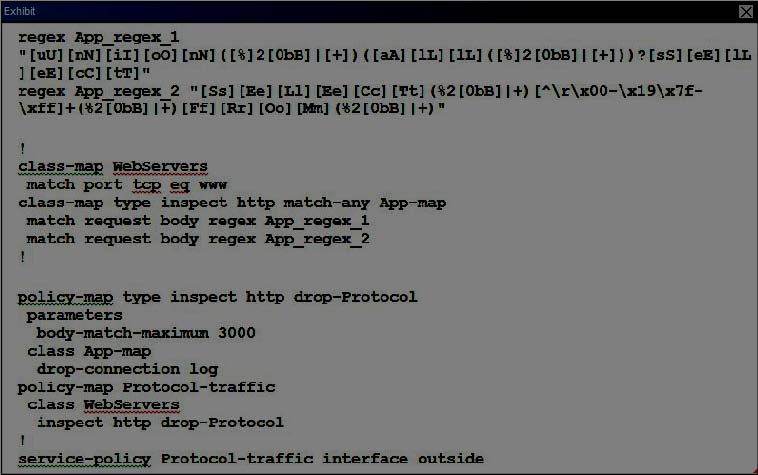
What is the best description of a unified ACL on a Cisco firewall?
What is the best description of a unified ACL on a Cisco firewall?
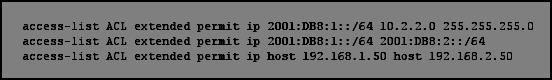
Which type of ACL is shown in this configuration?
You have completed this exercise when you have configured and successfully tested…
SIMULATION
You are the network security engineer for the Secure-X network. The company has recently detected
Increase of traffic to malware Infected destinations. The Chief Security Officer deduced that some
PCs in the internal networks are infected with malware and communicate with malware infected
destinations.
The CSO has tasked you with enable Botnet traffic filter on the Cisco ASA to detect and deny further
connection attempts from infected PCs to malware destinations. You are also required to test your
configurations by initiating connections through the Cisco ASA and then display and observe the
Real-Time Log Viewer in ASDM.
To successfully complete this activity, you must perform the following tasks:
* Download the dynamic database and enable use of it.
• Enable the ASA to download of the dynamic database
• Enable the ASA to download of the dynamic database.
• Enable DNS snooping for existing DNS inspection service policy rules..
• Enable Botnet Traffic Filter classification on the outside interface for All Traffic.
• Configure the Botnet Traffic Filter to drop blacklisted traffic on the outside interface. Use the
default Threat Level settings
NOTE: The database files are stored in running memory; they are not stored in flash memory.
NOTE: DNS is enabled on the inside interface and set to the HQ-SRV (10.10.3.20).
NOTE: Not all ASDM screens are active for this exercise.
• Verify that the ASA indeed drops traffic to blacklisted destinations by doing the following:
• From the Employee PC, navigate to http://www.google.com to make sure that access to the
Internet is working.
• From the Employee PC, navigate to http://bot-sparta.no-ip.org. This destination is classified as
malware destination by the Cisco SIO database.
• From the Employee PC, navigate to http://superzarabotok-gid.ru/. This destination is classified as
malware destination by the Cisco SIO database.
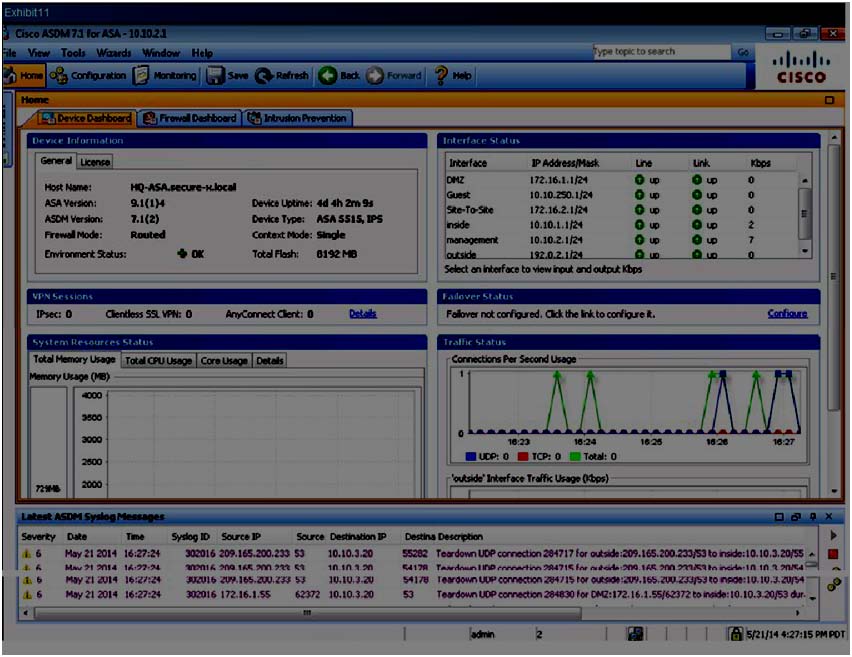
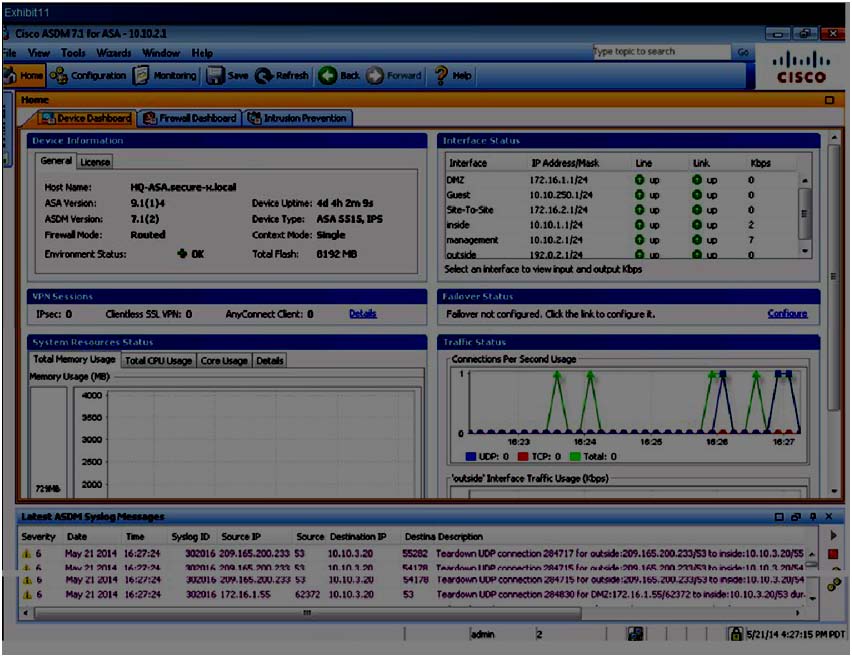
• From Admin PC, launch ASDM to display and observe the Real-Time Log Viewer.
You have completed this exercise when you have configured and successfully tested Botnet traffic
filter on the Cisco ASA.
You have been tasked with implementing dynamic network object NAT with PAT on a Cisco AS
SIMULATION
You are a network security engineer for the Secure-X network. You have been tasked with
implementing dynamic network object NAT with PAT on a Cisco AS