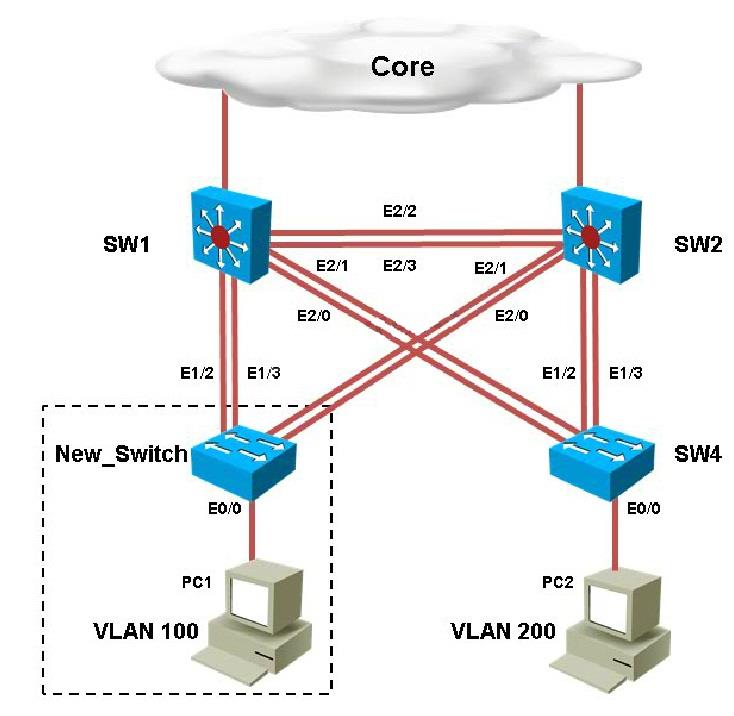
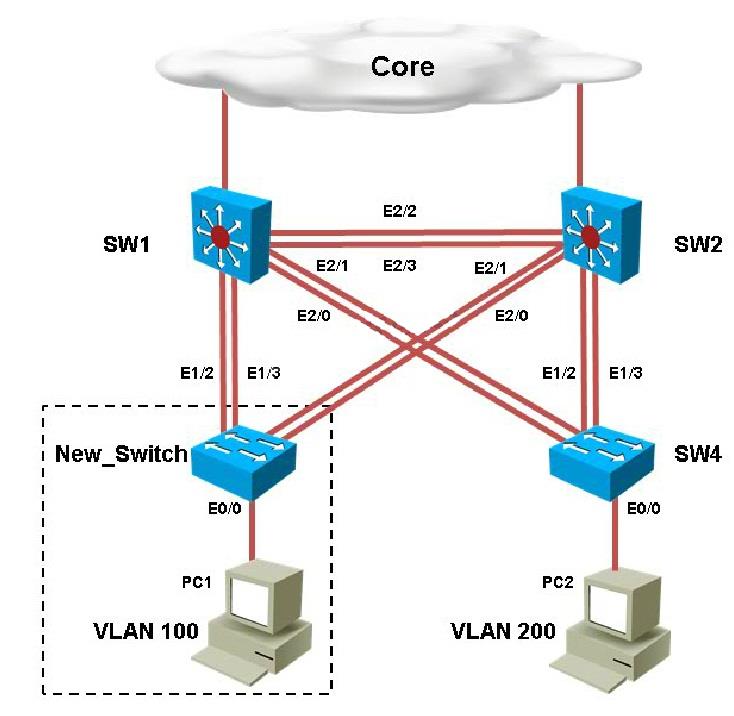
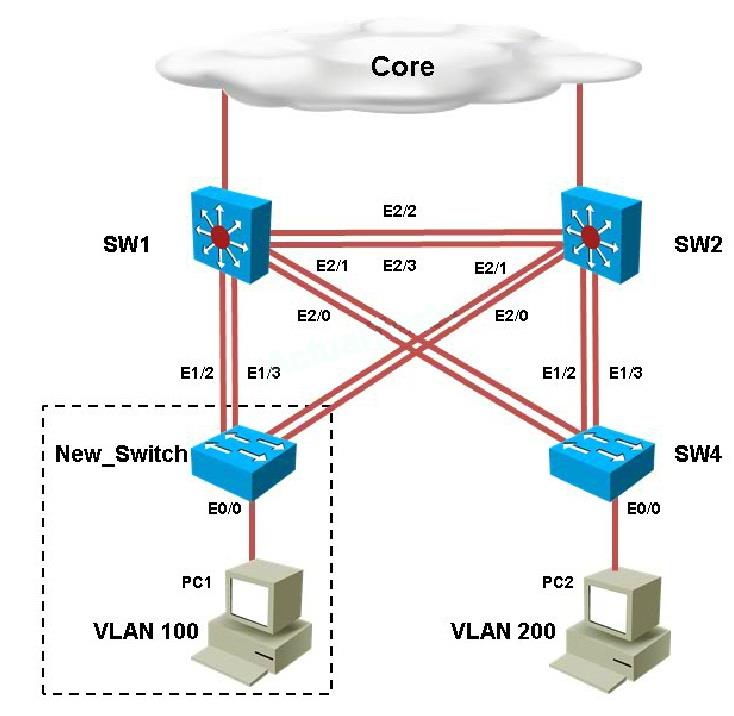
Which of the configuration is correct?
You have been asked to install and configure a new switch in a customer network. Use the
console access to the existing and new switches to configure and verify correct device
configuration.
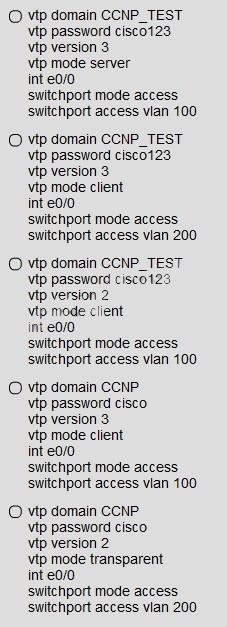
You are connecting the New_Switch to the LAN topology; the switch has been partially configured
and you need to complete the rest of configuration to enable PC1 communication with PC2. Which
of the configuration is correct?
which configured VLAN are untagged frames sent over trunk between SW1 and SW2?
Which configuration step is valid?
You have been asked to install and configure a new switch in a customer network. Use the
console access to the existing and new switches to configure and verify correct device
configuration.
You are adding new VLANs. VLAN500 and VLAN600 to the topology in such way that you need to
configure SW1 as primary root for VLAN 500 and secondary for VLAN 600 and SW2 as primary
root for VLAN 600 and secondary for VLAN 500. Which configuration step is valid?
Which of the following configuration steps will allow creating private VLANs?
You have been asked to install and configure a new switch in a customer network. Use the
console access to the existing and new switches to configure and verify correct device
configuration.
Examine the VTP configuration. You are required to configure private VLANs for a new server
deployment connecting to the SW4 switch. Which of the following configuration steps will allow
creating private VLANs?
What is the solution to avoid the snooping database from being rebuilt after every device reboot?
A Cisco Catalyst switch that is prone to reboots continues to rebuild the DHCP snooping
database. What is the solution to avoid the snooping database from being rebuilt after every
device reboot?
what a user has access to?
Which portion of AAA looks at what a user has access to?
Which command creates a login authentication method named "login" that will primarily use RADIUS and
Which command creates a login authentication method named “login” that will primarily use
RADIUS and fail over to the local user database?
Which solution ensures that the server maintains network reachability in the future?
A server with a statically assigned IP address is attached to a switch that is provisioned for DHCP
snooping. For more protection against malicious attacks, the network team is considering enabling
dynamic ARP inspection alongside DHCP snooping. Which solution ensures that the server
maintains network reachability in the future?
Which configuration must be made before the private VLAN is configured?
A network engineer wants to ensure Layer 2 isolation of customer traffic using a private VLAN.
Which configuration must be made before the private VLAN is configured?
Which statement describes the outcome of this scenario?
DHCP snooping and IP Source Guard have been configured on a switch that connects to several
client workstations. The IP address of one of the workstations does not match any entries found in
the DHCP binding database. Which statement describes the outcome of this scenario?