How can you ensure that only the MAC address of a server is allowed by switch port Fa0/1?
How can you ensure that only the MAC address of a server is allowed by switch port Fa0/1?
What should be part of a comprehensive network security plan?
What should be part of a comprehensive network security plan?
What is the purpose of the switchport command?
What is the purpose of the switchport command?
Switch(config-if)# switchport port-security maximum 1
Switch(config-if)# switchport port-security mac-address 0018.DE8B.4BF8
What are two recommended ways of protecting network device configuration files from outside network security t
What are two recommended ways of protecting network device configuration files from
outside network security threats? (Choose two.)
This information should, however, be accessible to devices on the internal networks of RT
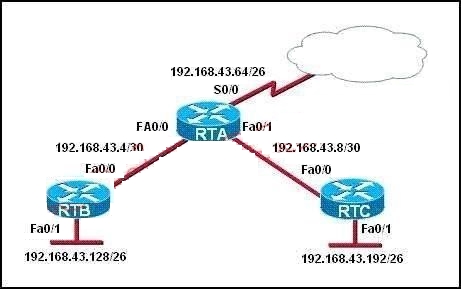
Refer to the exhibit.
For security reasons, information about RTA, including platform and IP addresses, should not be
accessible from the Internet. This information should, however, be accessible to devices on the
internal networks of RTA.
Which command or series of commands will accomplish these objectives?
which of the following attacks can Message Authentication Code (MAC) shield your network?
From which of the following attacks can Message Authentication Code (MAC) shield your
network?
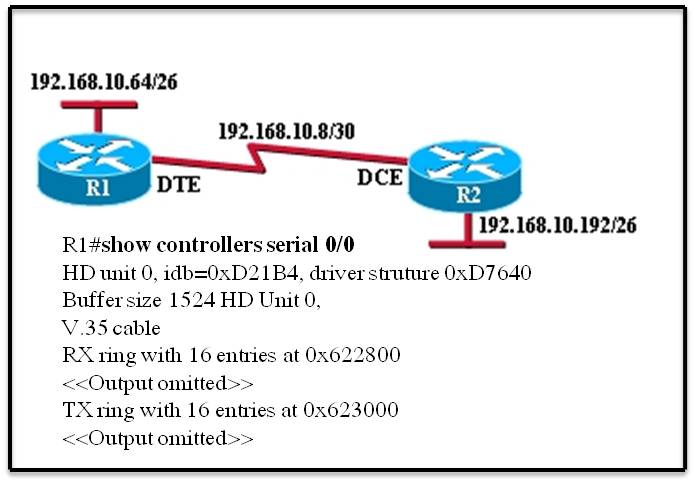
what could be the problem?
What is the cause of this problem?
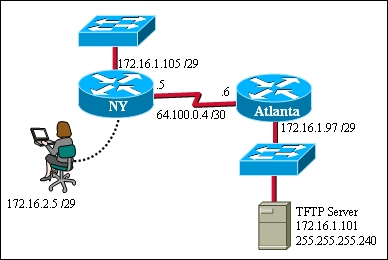
Refer to the exhibit.
A TFTP server has recently been installed in the Atlanta office. The network administrator is
located in the NY office and has made a console connection to the NY router.After establishing
the connection they are unable to backup the configuration file and IOS of the NY router to the
TFTP server. What is the cause of this problem?
what could cause congestion on this LAN?
If a host experiences intermittent issues that relate to congestion within a network while
remaining connected, what could cause congestion on this LAN?
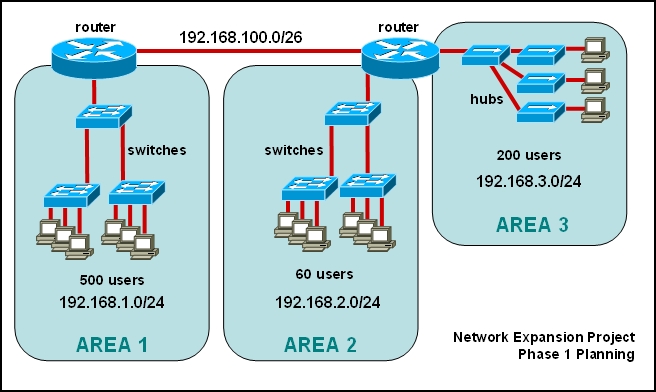
What are three problems with this design?
Refer to the exhibit.
The junior network support staff provided the diagram as a recommended configuration for the
first phase of a four-phase network expansion project. The entire network expansion will have
over 1000 users on 14 network segments and has been allocated this IP address space.
192.168.1.1 through 192.168.5.255
192.168.100.1 through 192.168.100.255
What are three problems with this design? (Choose three.)