Which two protocols could be used during this communication?
The network administrator is using a Windows PC application that is called putty.exefor remote
communication to a switch for network troubleshooting. Which two protocols could be used
during this communication? (Choose two.)
which OSI layer should the administrator begin troubleshooting?
A network administrator cannot connect to a remote router by using SSH. Part of the show
interfaces command is shown.
router#show interfaces
Serial0/1/0 is up, line protocol is down
At which OSI layer should the administrator begin troubleshooting?
Which of the following statements are TRUE regarding Cisco access lists?
Which of the following statements are TRUE regarding Cisco access lists? (Choose two.)
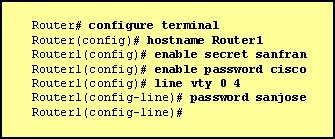
what password or password sequence is required for the administrator to access privileged mode on Router1?
What is the purpose of the last command entered?
The following commands are entered on the router:
Burbank(config)# enable secret fortress
Burbank(config)# line con 0
Burbank(config-line)# login
Burbank(config-line)# password n0way1n
Burbank(config-line)# exit
Burbank(config)# service password-encryption
What is the purpose of the last command entered?
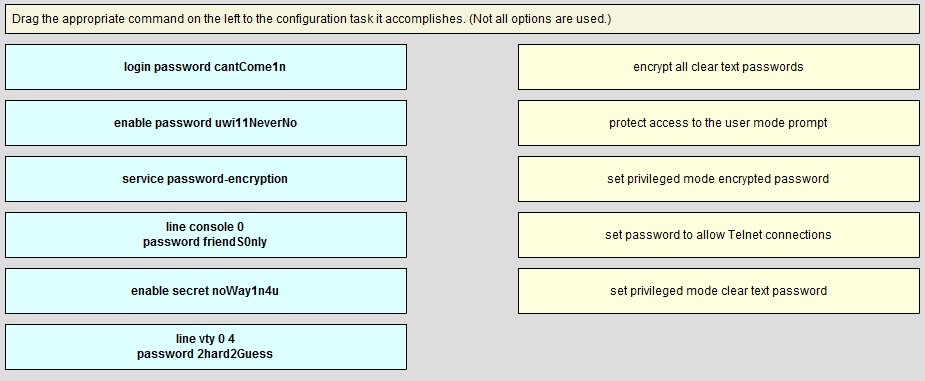
Drag the appropriate command on the left to the configuration task it accomplished.
What is the effect of using the service password-encryption command?
What is the effect of using the service password-encryption command?
What must be done to accomplish this?
An administrator has connected devices to a switch and, for security reasons, wants the
dynamically learned MAC addresses from the address table added to the running configuration.
What must be done to accomplish this?
which three configuration steps should be performed on the switch to prevent this?
A company has placed a networked PC in a lobby so guests can have access to the corporate
directory.
A security concern is that someone will disconnect the directory PC and re-connect their laptop
computer and have access to the corporate network. For the port servicing the lobby, which
three configuration steps should be performed on the switch to prevent this? (Choose three.)
Why would a network administrator configure port security on a switch?
Why would a network administrator configure port security on a switch?