which technology is IPsec required for a site-to-site enterprise WAN/MAN architecture?
For which technology is IPsec required for a site-to-site enterprise WAN/MAN architecture?
Which technology can ensure data confidentiality, data integrity, and authentication across a public IP.networ
Which technology can ensure data confidentiality, data integrity, and authentication across a public IP
network?
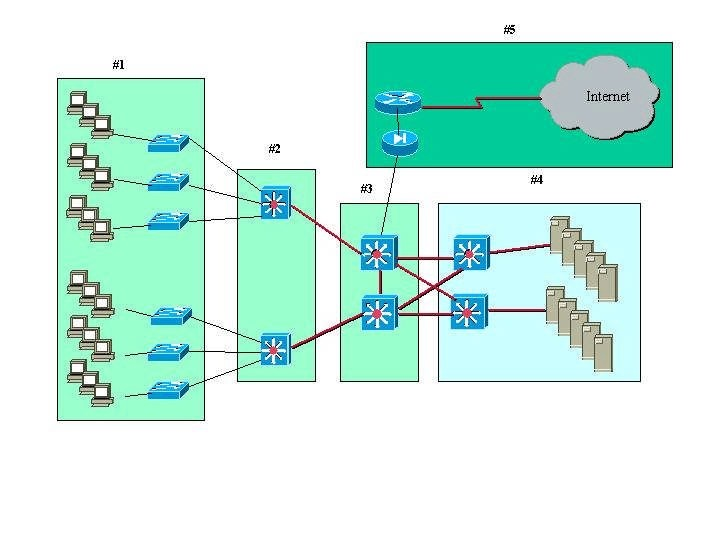
Which numbered box represents the core layer?
Which two link state routing protocols support IPv6 routing?
Which two link state routing protocols support IPv6 routing? (Choose two.)
Which of these is the next step after the design phase in the PPDIOO process?
Which of these is the next step after the design phase in the PPDIOO process?
Which command should you use?
You are performing an audit of a customer’s existing network and need to obtain the following router
information:
interfaces
running processes
IOS image being executed
Which command should you use?
What is the benefit of VLSM?
What is the benefit of VLSM?
Which two statements represent advantages that the top-down network design process has over the.bottom-up netw
Which two statements represent advantages that the top-down network design process has over the
bottom-up network design process? (Choose two.)
What is the benefit of deploying a gatekeeper in an H.323 IP telephony network?
What is the benefit of deploying a gatekeeper in an H.323 IP telephony network?
Which three of these are layers in the Cisco SONA Architecture?
Which three of these are layers in the Cisco SONA Architecture? (Choose three.)