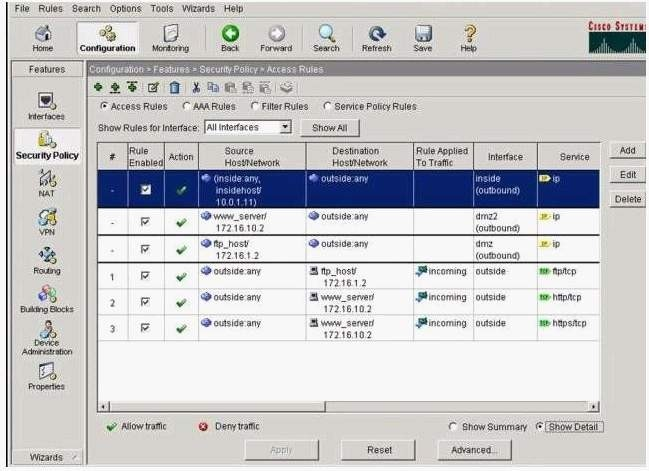
which of the following traffic is permitted based on the current Access Rules?
CSA protects your host by:
CSA protects your host by:
What is the most likely cause of this problem?
The key lengths for DES and 3DES, respectively, are:
The key lengths for DES and 3DES, respectively, are:
Which of the following are valid RADIUS packet flows’C indicates the user (such as a wireless laptop), N
Which of the following are valid RADIUS packet flows’C indicates the user (such as a wireless laptop), N indicates the NAS, and S indicates an ACS Server(Choose 2)
Which type of attacks can be monitored and mitigated by CS-MARS using NetFlow data?
Which type of attacks can be monitored and mitigated by CS-MARS using NetFlow data?
Which access control model provides access to system resources based on the job function of the user or the ta
Which access control model provides access to system resources based on the job function of the user or the tasks that the user has been assigned?
Which command or commands on the Cisco IOS router would you use to verify that the web server is working corre
Refer to the exhibit.
A user located at the PC with IP address 198.51.100.2 is complaining that the PC is unable to access any web server, including cisco.com. As a network administrator, you may attempt to troubleshoot the problem by logging into the router, which is the user’s default gateway, and attempting to access cisco.com. Which command or commands on the Cisco IOS router would you use to verify that the web server is working correctly?
What is the function of the switch(config-if)# switchport port-security mac-address sticky command?
What is the function of the switch(config-if)# switchport port-security mac-address sticky command?
which three commands on the router would accomplish these goals?
CustomerA has set up a central syslog server to receive all syslog messages from its routers. The IP address of this central server is 1.1.1.1, and the customer wants all messages of level “error” and above to be sent there. In addition, it wants all messages of level “warning” and above to be stored locally on the router. Assuming logging is already enabled, which three commands on the router would accomplish these goals? (Choose three.)