what MAC address are these messages sent?
A network administrator is using a LAN analyzer to troubleshoot OSPF router exchange messages sent to ALL OSPF ROUTERS. To what MAC address are these messages sent?
which one of the following is NOT a valid configuration option?
When configuring a multipoint GRE (Mgre) tunnel interface, which one of the following is NOT a valid configuration option?
what appears to be the issue why the remote user can not create a web session with the dmz1_host?
An administrator is troubleshooting a new ASDM configured security appliance. A remote user is trying to establish a web session with the dmz1_host and the in_host from a PC on the outside network. The remote user is able to establish a FTP connection with the in_host successfully from the outside. However, they are unable to connect to the dmz1_host with an IP address of 192.168.1.4 from their outside PC. The administrator checked the access-lists and they were correct. The next step was to check the security appliance interfaces and NAT configuration screens. From information present on the ASDM screens, what appears to be the issue why the remote user can not create a web session with the dmz1_host?
Which of the following statements that describe the PPTP protocol is incorrect?
Which of the following statements that describe the PPTP protocol is incorrect?
Which best represents a typical attack that takes advantage of RFC 792, ICMP Type 3 messages?
Which best represents a typical attack that takes advantage of RFC 792, ICMP Type 3 messages?
Which operational function within the FWSM handles this issue?
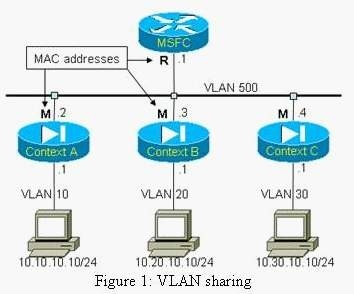
Figure 1 represents 3 security contexts all sharing a common VLAN (500)-a single IP subnet corresponds to that VLAN.This is equivalent to connecting three security appliances using an Ethernet switch.A property of the FWSM makes all interfaces across the entire module use only one global MAC address (‘M’ in Figure 1).This is usually not a problem, until multiple contexts start sharing an interface.Which operational function within the FWSM handles this issue?
Which two steps does a receiver perform to validate a message using HMAC?
Which two steps does a receiver perform to validate a message using HMAC? (Choose two.)
which one of the following is NOT a required step?
When enrolling a Cisco IOS router to a CA server using the SCEP protocol, which one of the following is NOT a required step?