Which building blocks make up the Adaptive Threat Defense phase of Cisco SDN strategy?
Which building blocks make up the Adaptive Threat Defense phase of Cisco SDN strategy?
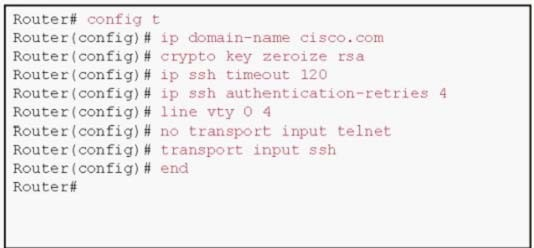
which can represent the highest security risk?
Referring to the partial router configuration shown, which can represent the highest security risk?
Which two encryption algorithms are commonly used to encrypt the contents of a message?
Which two encryption algorithms are commonly used to encrypt the contents of a message? (Choose two.)
Why is implementing NAT over the Internet supporting this type of application an issue?
A mission critical server application embeds a private IP address and port number in the payload of packets that is used by the client to reply to the server. Why is implementing NAT over the Internet supporting this type of application an issue?
what will a router do with incoming network traffic when the Cisco IOS IPS software fails to build a SME?
By default, what will a router do with incoming network traffic when the Cisco IOS IPS software fails to build a SME?
Which two Cisco AutoSecure features are not supported in the One-Step Lockdown feature found in Cisco SDM Vers
Which two Cisco AutoSecure features are not supported in the One-Step Lockdown feature found in Cisco SDM Version 2.2a? (Choose two.)
Which of these is true regarding IKE Phase 2?
Which of these is true regarding IKE Phase 2?
Which three components are used in the PKI environment?
Which three components are used in the PKI environment? (Choose three.)
Which Cisco IOS command or setting does the configuration need to get SSH to work?
What is the key function of a comprehensive security policy?
What is the key function of a comprehensive security policy?