Which two features block traffic that is sourced from n…
Which two features block traffic that is sourced from non-topological IPv6 addresses? (Choose two.)
Which security operations management best practice shou…
Which security operations management best practice should be followed to enable appropriate
network access for administrators?
which type of PVLAN port should be used for each host?
which option must you configure in addition to the targ…
which option must you associate it?
Hotspot Questions
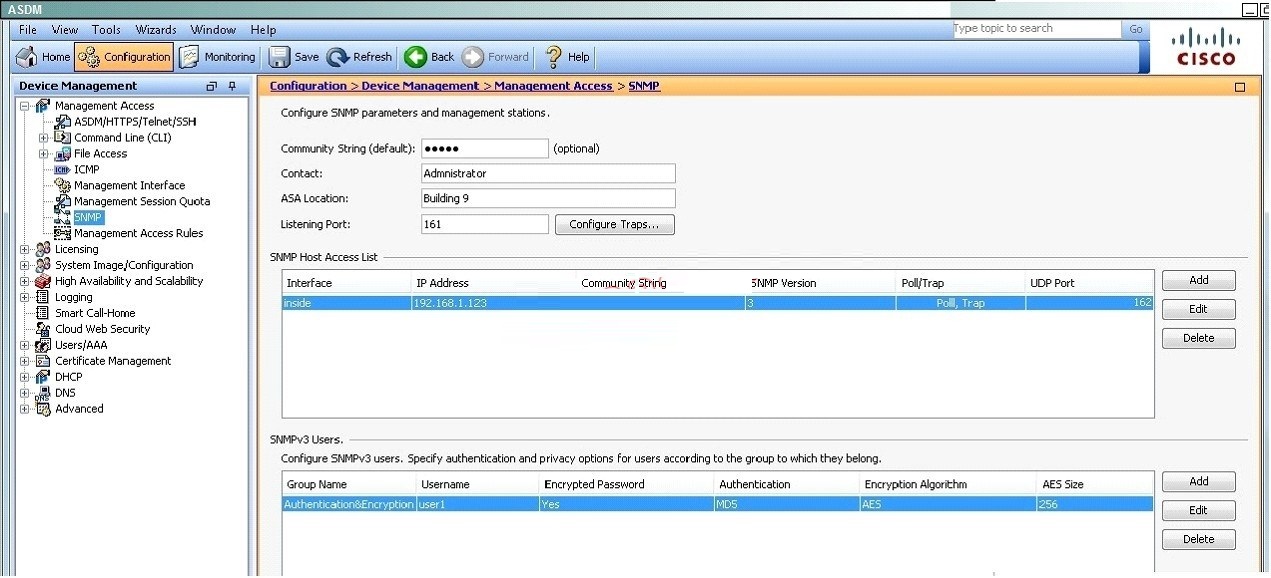
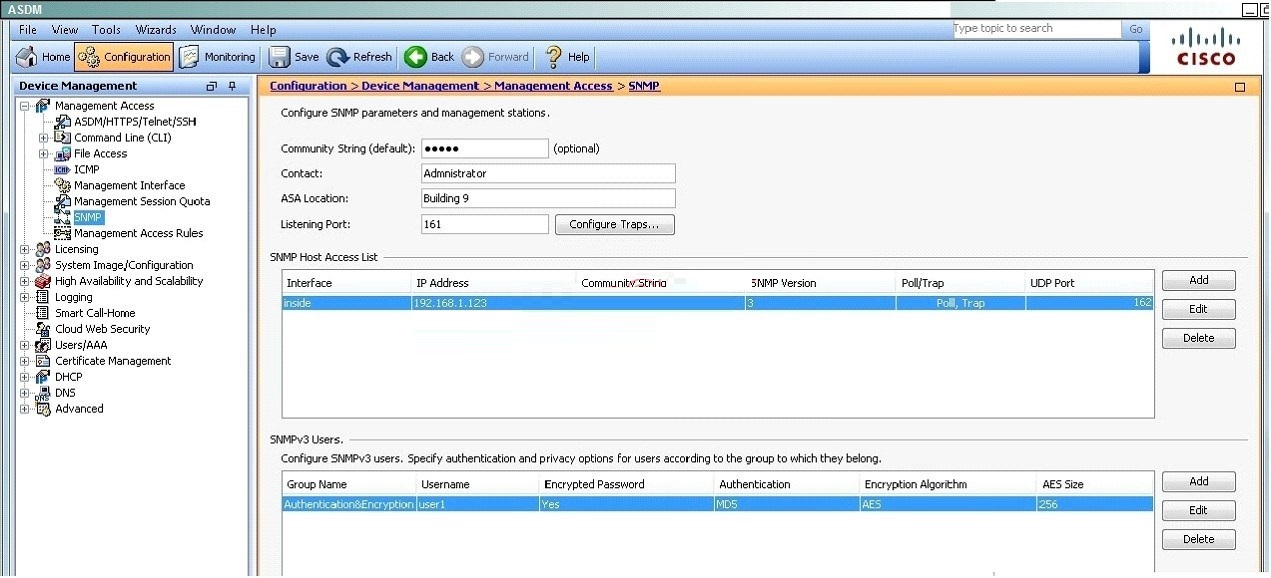
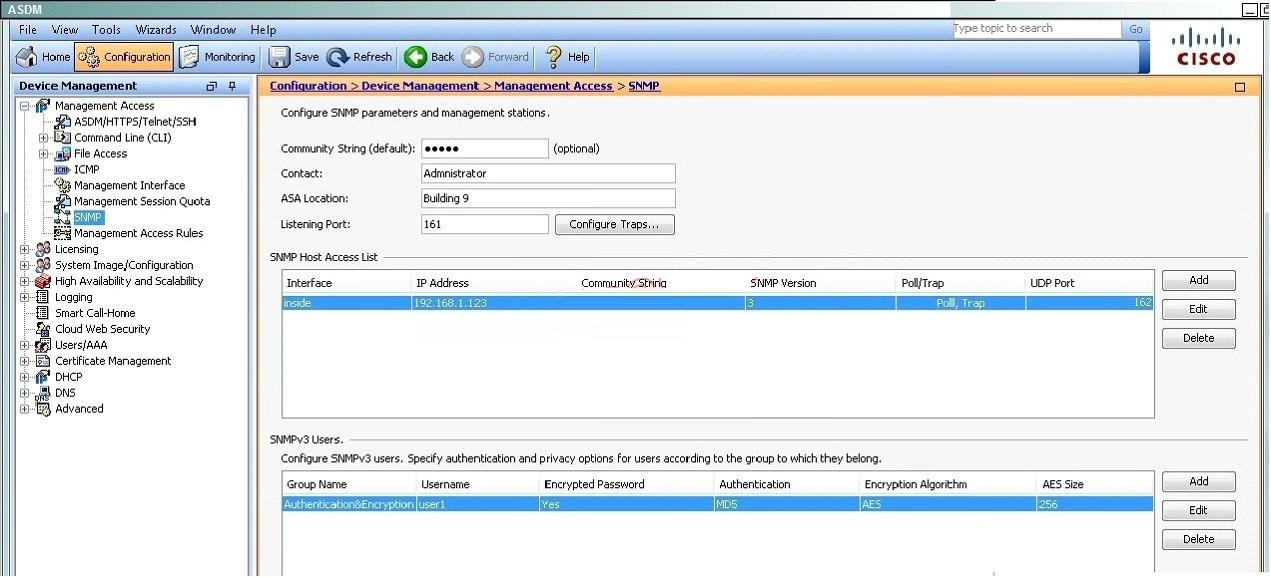
SNMP users have a specified username, a group to which the user belongs, authentication
password, encryption password, and authentication and encryption algorithms to use. The
authentication algorithm options are MD5 and SHA. The encryption algorithm options are DES,
3DES, andAES (which is available in 128,192, and 256 versions). When you create a user, with
which option must you associate it?
Which statement about how the Cisco ASA supports SNMP i…
What is the result?
Which command configures the SNMP server group1 to enab…
Which command configures the SNMP server group1 to enable authentication for members of the
access list east?
Which two considerations must an administrator take int…
An administrator is deploying port-security to restrict traffic from certain ports to specific MAC
addresses. Which two considerations must an administrator take into account when using the
switchport port-security mac-address sticky command? (Choose two.)
Which set of commands creates a message list that inclu…
Which set of commands creates a message list that includes all severity 2 (critical) messages on a
Cisco security device?