Which two commands can protect against this problem?
A rogue device has connected to the network and has become the STP root bridge, which has
caused a network availability issue.
Which two commands can protect against this problem? (Choose two.)
which statement describes how you will ensure that retu…
You are the administrator of a multicontext transparent-mode Cisco ASA that uses a shared
interface that belongs to more than one context. Because the same interface will be used within all
three contexts, which statement describes how you will ensure that return traffic will reach the
correct context?
which two modes is zone-based firewall high availabilit…
In which two modes is zone-based firewall high availability available? (Choose two.)
Which statement about the minimum requirements to set u…
Your company is replacing a high-availability pair of Cisco ASA 5550 firewalls with the newer Cisco
ASA 5555-X models. Due to budget constraints, one Cisco ASA 5550 will be replaced at a time.
Which statement about the minimum requirements to set up stateful failover between these two
firewalls is true?
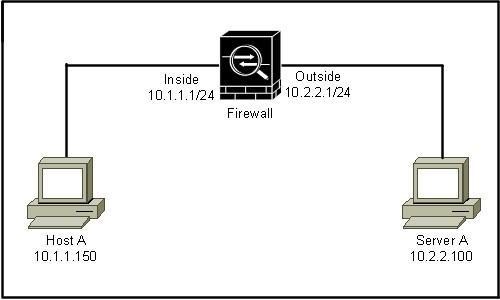
Which command captures http traffic from Host A to Server A?
Which two options are purposes of the packet-tracer command?
Which two options are purposes of the packet-tracer command? (Choose two.)
Which three options are default settings for NTP parame…
Which three options are default settings for NTP parameters on a Cisco ASA? (Choose three.)
which username and password grants you full access?
An administrator installed a Cisco ASA that runs version 9.1. You are asked to configure the firewall
through Cisco ASDM.
When you attempt to connect to a Cisco ASA with a default configuration, which username and
password grants you full access?
Which two features does Cisco Security Manager provide?
Which two features does Cisco Security Manager provide? (Choose two.)
Which two configurations are necessary to enable passwo…
Which two configurations are necessary to enable password-less SSH login to an IOS router?
(Choose two.)