Which five system management and reporting protocols are supported by the Cisco Intrusion Prevention System?
Which five system management and reporting protocols are supported by the Cisco Intrusion Prevention
System? (Choose five.)
What is the likely cause of the intermittent delays?
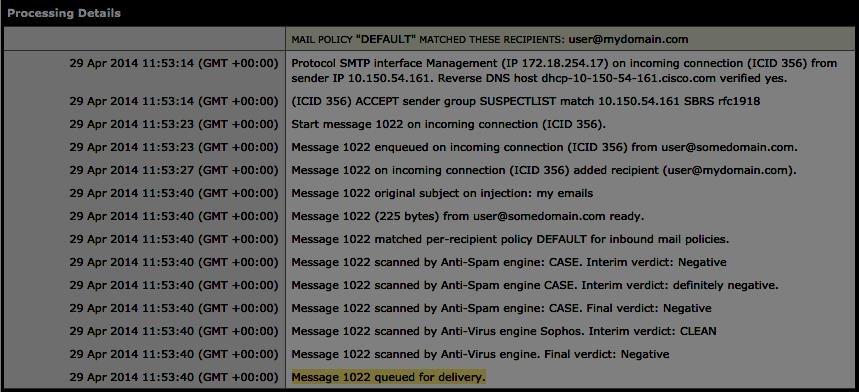
Refer to the exhibit.
The system administrator of mydomain.com received complaints that some messages that were sent
from sender user@somedomain.com were delayed. Message tracking data on the sender shows that an
email sample that was received was clean and properly delivered. What is the likely cause of the
intermittent delays?
Which tool on the Cisco Email Security gateway can you use to debug or emulate the flow that a message takes t
A system administrator wants to know if the email traffic from a remote partner will activate special
treatment message filters that are created just for them. Which tool on the Cisco Email Security gateway
can you use to debug or emulate the flow that a message takes through the work queue?
Which command verifies that CWS redirection is working on a Cisco IOS router?
Which command verifies that CWS redirection is working on a Cisco IOS router?
Which two commands are used to verify that CWS redirection is working on a Cisco ASA appliance?
Which two commands are used to verify that CWS redirection is working on a Cisco ASA appliance?
(Choose two.)
Which two modes does Cisco recommend using to configure for this?
A user is deploying a Cisco IPS appliance in a data center to mitigate most attacks, including atomic
attacks. Which two modes does Cisco recommend using to configure for this? (Choose two.)
Which statement about Cisco IPS Manager Express is true?
Which statement about Cisco IPS Manager Express is true?
Which four rows identify the switch behavior in correlation to the redirect method?
Which four rows exhibit the correct WCCP service to protocol assignments?
Which three protocols are required when considering firewall rules for email services using a Cisco Email Secu
Which three protocols are required when considering firewall rules for email services using a Cisco Email
Security Appliance? (Choose three.)