What are the three flag bits in an IPv4 header?
What are the three flag bits in an IPv4 header? (Choose three.)
which of the following objective?
In ISO 27002, access control code of practice for Information Security Management
serves which of the following objective?
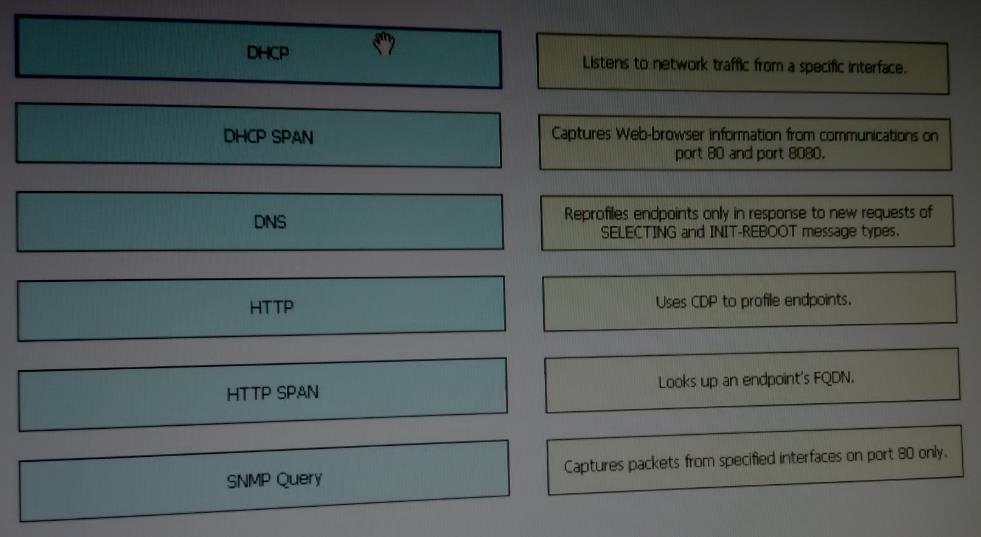
Drag each ISE probe on the left to the matching statement on the right.
What security element must an organization have in place before it can implement a security audit and validate
What security element must an organization have in place before it can implement a
security audit and validate the audit results?
What are two functions that ESMTP application inspection provides when enabled on the ASA?
What are two functions that ESMTP application inspection provides when enabled on
the ASA? (Choose two.)
Which two statements about BPDU guard and root guard are true?
Which two statements about BPDU guard and root guard are true? (Choose two.)
Which of the following are two valid TLS message content types?
Which of the following are two valid TLS message content types? (Choose two.)
What are three features that are enabled by generating Change of Authorization (CoA) requests in a push model?
What are three features that are enabled by generating Change of Authorization (CoA)
requests in a push model? (Choose three.)
What is the first step in performing a risk assessment?
What is the first step in performing a risk assessment?
which two statements about the configuration are true?
When you enable the same-security-traffic permit Inter-interface command on the ASA,
which two statements about the configuration are true? (Choose two.)