what configuration can you apply to the router to prevent high CPU usage when the OID is queried?
Drag and drop the web attack types from the left to the corresponding descriptions of…
Which two statements about the TACACS+ protocol are true?
Which two statements about the TACACS+ protocol are true? (Choose two.)
which two statements are correct?
Which two statements about fast SSID changing on a WLC are true?
Which two statements about fast SSID changing on a WLC are true? (Choose two.)
Which three options are methods of load-balancing data in an ASA cluster environment?
Which three options are methods of load-balancing data in an ASA cluster environment?
(Choose three.)
Drag each OSPF security feature on the left to its description on the right.
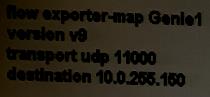
Which configuration is required to enable the exporter?
Which two statements about IPv6 Neighbor Solicitation Messages are true?
Which two statements about IPv6 Neighbor Solicitation Messages are true? (Choose
two.)
Which two ICMP types must be allowed in a firewall to enable traceroutes through the firewall?
Which two ICMP types must be allowed in a firewall to enable traceroutes through the
firewall? (Choose two.)