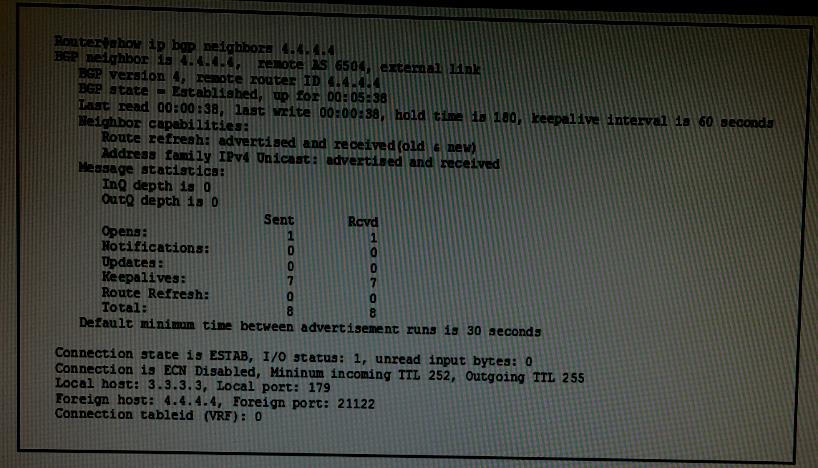
What is the maximum number of hops from the device that generated the given output to its BGP neighbor at 4.4.
Which two statements about 802.1x authentication with port security are true?
Which two statements about 802.1x authentication with port security are true? (Choose
two.)
Which as-path access-list regular expression should be applied on R2 as a neighbor filter list to only allow u
which type of authentication will it use?
If an ASA device is configured as a remote access IPsec server with RADIUS
authentication and password management enabled, which type of authentication will it
use?
What SNMFV3 command disables descriptive error messages?
What SNMFV3 command disables descriptive error messages?
Which statement about SNMP control plane policing is true?
Which statement about SNMP control plane policing is true?
Which two of these are things an attacker can do with an encrypted RC4 data stream?
Which two of these are things an attacker can do with an encrypted RC4 data stream?
(Choose two.)
What feature can you implement on R1 to make this configuration possible?
Refer to the exhibit.
You have configured two route-map instances on R1. which passes traffic from switch 1
on both VLAN 1 and VLAN 2 You wish to ensure that * The first route-map instance
matches packets from VLAN 1 and sets the next hop to 3232:2/128. * The second routemap instance matches packets from VLAN 2 and sets the next hop to 3232:3/128. What
feature can you implement on R1 to make this configuration possible?
which two locations?
When configuring Cisco IOS Firewall CBAC operations on Cisco routers, the “inspection
rule” can be applied at which two locations? (Choose two)
what is the appropriate urgency level for remediation?
Refer to the exhibit.
You have received an advisory that your organization could be running a vulnerable
product. Using the Cisco Systems Rapid Risk Vulnerability Response Model, you
determine that * Your organization is running an affected product on a vulnerable
version of code * The vulnerable component is enabled and there is no feasible
workaround. * There is medium confidence of an attack without significant collateral
damage to the organization. According to the model, what is the appropriate urgency
level for remediation?